Another malicious campaign has been identified within the npm ecosystem, leveraging Skuld Infostealer—a notorious malware targeting developers. Researchers at Socket reported that the attacks are linked to malicious activity from a profile operating under the alias “k303903.” Both individual developers and entire companies have been affected.
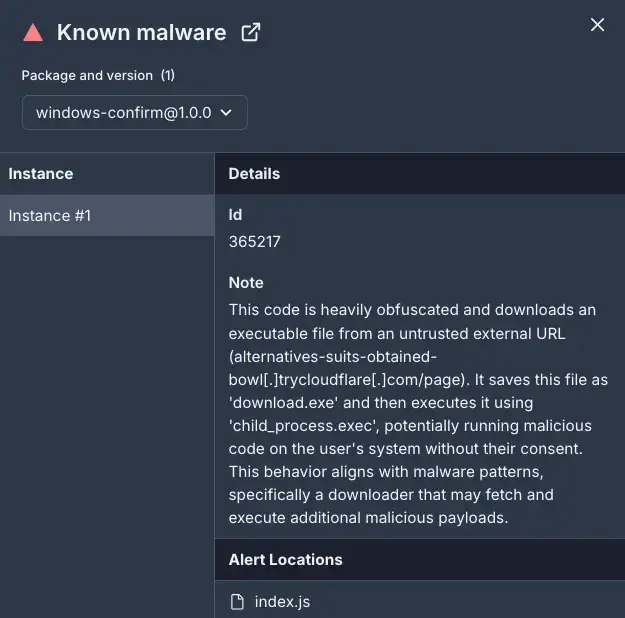
The attacker utilized npm packages disguised as legitimate tools, including windows-confirm, windows-version-check, downloadsolara, and solara-config. These packages were downloaded over 600 times before being removed from the registry.
According to Socket, the campaign employed code obfuscation, typosquatting techniques, and standard malicious software. The report also highlighted that Skuld’s reappearance in npm underscores the cyclical nature of such attacks.
Skuld Infostealer is particularly dangerous due to its ability to exfiltrate passwords, cookies, confidential files, and browsing history from Chromium-based (e.g., Chrome) and Gecko-based (e.g., Firefox) browsers. The malware’s code is obfuscated using Obfuscator.io. Upon installation of the compromised packages, the payload is downloaded from fake domains designed to mimic legitimate Cloudflare resources. Victim data is then exfiltrated via Discord webhooks, masquerading as legitimate communications.
Experts emphasize that such attacks exploit trust in supply chains. By masquerading as useful tools, the attackers covertly deployed malicious code onto developers’ machines.
The npm administration promptly removed the malicious packages, but the impact on users remains substantial. Stolen credentials, tokens, and other sensitive information could potentially be exploited long after the attack has ended. This incident once again highlights the vulnerabilities of developer platforms, where it is alarmingly easy to distribute malicious code undetected.


