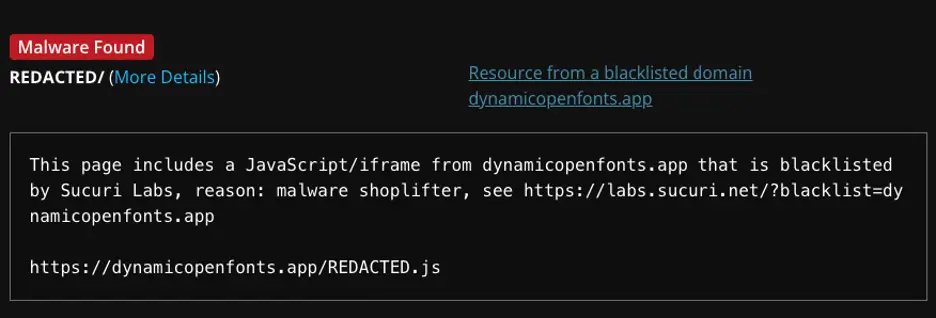
Researchers at Sucuri uncovered a new attack targeting websites running on the Magento platform. Cybercriminals are deploying malicious JavaScript to steal data from the payment pages of online stores. This attack is particularly insidious due to its sophisticated obfuscation techniques, which make detection significantly more challenging.
The script operates in two distinct ways: it either generates a fake form to capture card details or extracts information directly from payment fields. Once collected, the data is encrypted and transmitted to the attackers’ server. Magento sites are frequently targeted by hackers because of their popularity and the high volume of payment data they process.
The malicious script activates exclusively on pages containing the keyword “checkout” in the URL, while excluding pages with “cart.” After completing its primary task, the malware uses the Magento API to gather additional data such as usernames, addresses, email addresses, phone numbers, and other sensitive information.
To encrypt the stolen data, the attackers employ an XOR method with the key “script,” after which the data is encoded in Base64 and sent to a remote server.
Experts advise site administrators to conduct regular security audits, update software consistently, implement a web application firewall (WAF), and use unique, strong passwords. Employing file integrity monitoring can also help identify unauthorized changes promptly.
While Magento remains a popular platform, its vulnerabilities continue to attract the attention of cybercriminals. Without robust protective measures, such attacks could lead to the compromise of thousands of users’ data.


