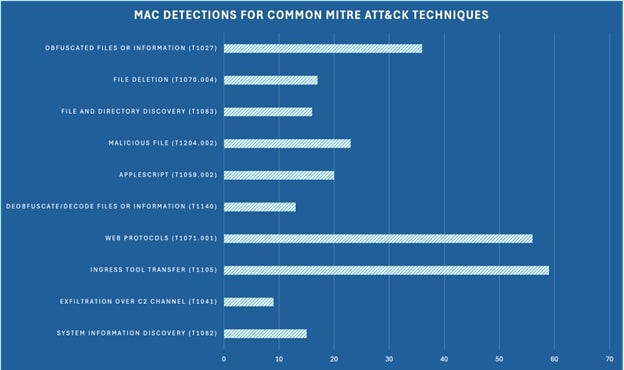
Number of Detections for top Mac related TTPs
In recent years, the threat landscape for macOS has evolved significantly, as noted by Trellix. According to StatCounter, macOS usage grew by 2% when comparing the period from January 2021 to January 2023 with that from January 2023 to August 2024. The platform’s rising popularity among corporate users has drawn the attention of cybercriminals, from financially motivated groups to advanced persistent threat (APT) actors.
The appeal of macOS to malicious actors stems not only from the increased number of devices but also from the high profile of its users. Unlike point-of-sale terminals, where macOS is rarely encountered, it is often the operating system of choice for developers, cybersecurity experts, vice presidents, and senior executives. Accessing the devices of such users opens opportunities for fraudulent transactions, confidential data theft, or disabling internal digital security systems.
The proliferation of threats is further fueled by the increasing use of cross-platform programming languages, such as Golang, in creating malware. Unlike traditional languages like C++, which require significant code modification to run on different platforms, modern cross-platform languages allow macOS to be targeted with minimal effort.
One group particularly active in macOS attacks is the North Korean hacker group Lazarus. Since 2018, the group has distributed malware through fake cryptocurrency trading applications, as macOS is more prevalent among cryptocurrency users and enthusiasts. A prominent example is the GMERA malware, embedded in counterfeit platforms like “Union Crypto Trader.” Victims are lured in through phishing emails and sophisticated social engineering tactics. Once installed, the malware gains control over macOS systems via LaunchDaemons or LaunchAgents.
By 2020, Lazarus expanded its toolkit with cross-platform malware. The ElectroRAT campaign, conducted between 2020 and 2021, targeted cryptocurrency users across macOS, Windows, and Linux. The group created fake websites and online profiles to promote malicious applications on cryptocurrency forums. The malware provided backdoor access to victims’ systems.
Lazarus also launched supply chain attacks using XcodeSpy, aimed at macOS developers. Hackers embedded malicious scripts in open-source repositories, infecting developer systems when compiling compromised Xcode projects. This method not only granted access to development environments but also posed broader software security risks.
In 2022-2023, Lazarus intensified its focus on corporate targets. The group conducted phishing campaigns disguised as recruitment efforts, distributing signed malware masked as applicant files. Upon opening, these files installed tools to exfiltrate corporate data.
The group actively employs cross-platform programming languages such as Python, Golang, and Rust. In 2023, a malware named RustBucket was discovered—a multi-stage backdoor for macOS written in Rust. The program uses AppleScript to load the payload and employs LaunchAgents to establish persistence on the system.
Experts emphasize that the commonly held belief in macOS’s enhanced security is merely a reflection of its lower market share. As the platform gains popularity in the corporate sector, the frequency of targeted attacks on macOS users is rising. While this report highlights specific groups from certain regions, the range of threats is far broader.


