Processing command hashes
In July 2024, specialists from Kaspersky Lab discovered that more than ten Russian enterprises across various industries—ranging from engineering to medicine—had fallen victim to cyberattacks involving a previously unknown backdoor, Loki. The malware was developed using the popular open-source framework, Mythic.
Mythic was originally created as a tool for remote administration during cyberattack simulations and IT infrastructure security assessments. However, such frameworks are often exploited by cybercriminals for malicious purposes. Mythic allows for the creation of agents in various programming languages for any platform, with customizable functionalities tailored to developers’ needs. The criminals took advantage of these capabilities and crafted their own agent, named Loki, which makes detection and attribution significantly more difficult. Alongside this open-source framework, other publicly available utilities were also employed in the attacks.
Experts believe that in most cases, Loki infiltrated systems via emails containing malicious attachments. Once these files were opened by unsuspecting users, the backdoor would begin its activity. This is corroborated by telemetry data and file names such as “smeta_27.05.2024.exe,” “Na_soglasovanie_publikatsii_<enterprise>.rar,” and “PERECHEN_DOKUMENTOV.ISO.”
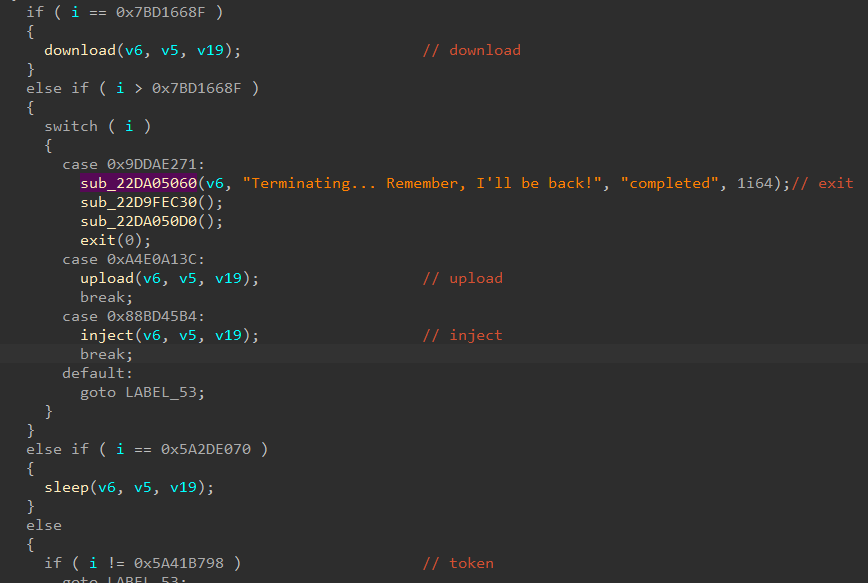
Loki poses a serious threat as it can execute a wide range of commands on an infected device. Attackers can upload and download any files, as well as launch malicious programs on the system. Attacks involving such backdoors often lead not only to the leakage of confidential data but also to the complete erasure of all files stored on the system.
The company noted that cybercriminals are increasingly relying on social engineering methods to breach corporate systems and gain access to critical information. To effectively safeguard against such threats, organizations are advised to implement multi-layered security strategies, regularly update systems and software, monitor network activity, and train employees to recognize signs of cyberattacks.


