Cybersecurity researchers have announced the creation of the first UEFI bootkit designed for Linux systems. Dubbed Bootkitty, this tool is regarded as a proof-of-concept (PoC) and, according to experts, has not yet been observed in real-world attacks. Also known as IranuKit, the bootkit was first uploaded to the VirusTotal platform on November 5, 2024.
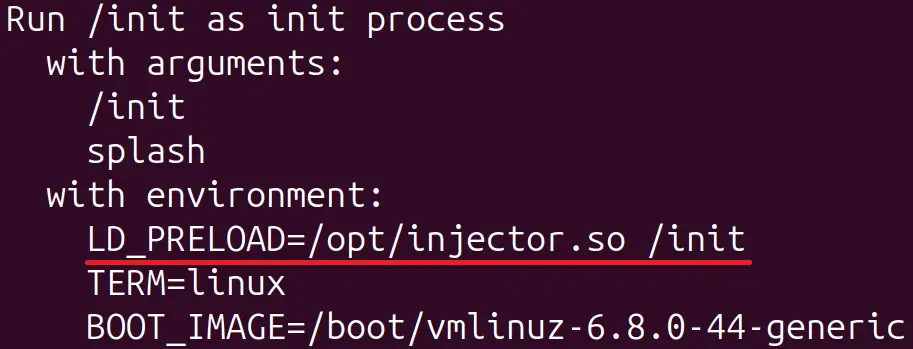
The primary purpose of Bootkitty is to disable the Linux kernel’s signature verification function and preload two ELF files via the init process, which is the first to run during system startup. According to experts at ESET, the bootkit’s capabilities pose a significant challenge to modern cybersecurity defenses.
This bootkit employs a self-signed certificate, preventing its execution on systems with Secure Boot enabled—unless attackers have preinstalled a controlled certificate. Even with Secure Boot active, Bootkitty can modify the kernel’s integrity verification functions in memory prior to launching the GRUB bootloader.
When Secure Boot is enabled, Bootkitty hooks into two UEFI authentication protocol functions, bypassing integrity checks. It then modifies three functions within the GRUB bootloader, allowing it to circumvent additional security measures. This showcases a critical vulnerability in contemporary systems.
During their investigation, ESET identified a related unsigned kernel module that deploys the ELF binary file BCDropper. This file, in turn, loads another unknown kernel module after system startup. The module’s features include classic rootkit capabilities, such as concealing files and processes and opening network ports.
Experts emphasize that Bootkitty dispels the notion that UEFI bootkits are a threat exclusive to Windows systems, highlighting the necessity of preparing for emerging Linux-targeted threats. This discovery could serve as a catalyst for advancements in securing Linux platforms against such sophisticated attacks.


