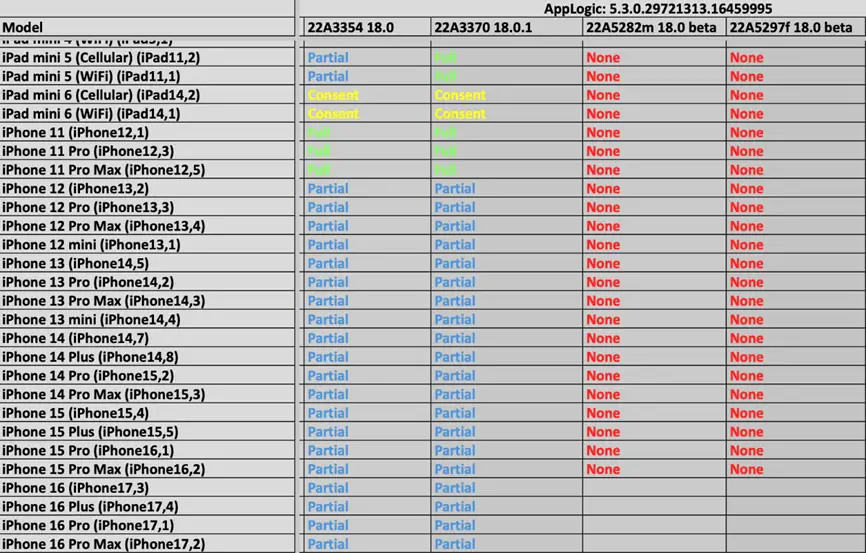
The GrayKey tool, widely used for unlocking phones and conducting digital forensic investigations, can no longer extract complete data from iPhones running iOS 18 and iOS 18.0.1. This revelation stems from leaked internal documents from Magnet Forensics, the company behind GrayKey. The documents, obtained by 404 Media, detail GrayKey’s capabilities and reveal that for modern devices, the tool provides only partial data access.
According to the materials, GrayKey can retrieve data from iPhone models ranging from the iPhone 12 to the latest iPhone 16 series on iOS 18.0 and iOS 18.0.1, but the access is limited. While specifics about the extracted data types remain undisclosed, previous reports suggest that “partial access” might include unencrypted files and metadata, such as file sizes and folder structures.
This leak highlights the ongoing clash between developers of digital forensic tools and mobile device manufacturers like Apple and Google. Apple, in particular, has bolstered its security measures with iOS 18, making device access increasingly challenging even for advanced tools like GrayKey.
The documents also indicate that GrayKey struggles with iPhones running beta versions of iOS 18.1. The reasons for this are unclear; it may be due to Magnet’s inability to adapt its technology in time or Apple’s implementation of substantial security enhancements.
Android devices remain another focus area for GrayKey, though the diversity of versions yields inconsistent results. For example, with the latest Google Pixel models, GrayKey offers only partial access, especially in the After First Unlock (AFU) state, where the device has been unlocked at least once since powering on.
![]()
The documents also reference a term called “AppLogic”, used by Magnet Forensics to describe the internal mechanics of its tools. However, details about this remain restricted to proprietary resources.
Similar leaks have previously surfaced for Magnet’s competitor, Cellebrite, whose documents highlighted its inability to extract data from many modern iPhones. Over time, however, companies like Cellebrite have managed to discover new vulnerabilities, underscoring the continuous tug-of-war between forensic tool developers and smartphone manufacturers.
This situation exemplifies the current state of data security: forensic companies innovate new methods to bypass protections, while Apple and Google rapidly close the vulnerabilities they exploit, perpetuating the cycle. Apple, Google, and Magnet Forensics declined to comment on the leak. Meanwhile, experts note that tools like GrayKey continue to be used by law enforcement agencies to access digital evidence, despite the increasing complexity of obtaining such data.
In June 2021, instructions detailing how law enforcement officials unlock iPhones were leaked. These documents described methods for bypassing security on powered-off or discharged iPhones, further illustrating the persistent battle over digital access.


