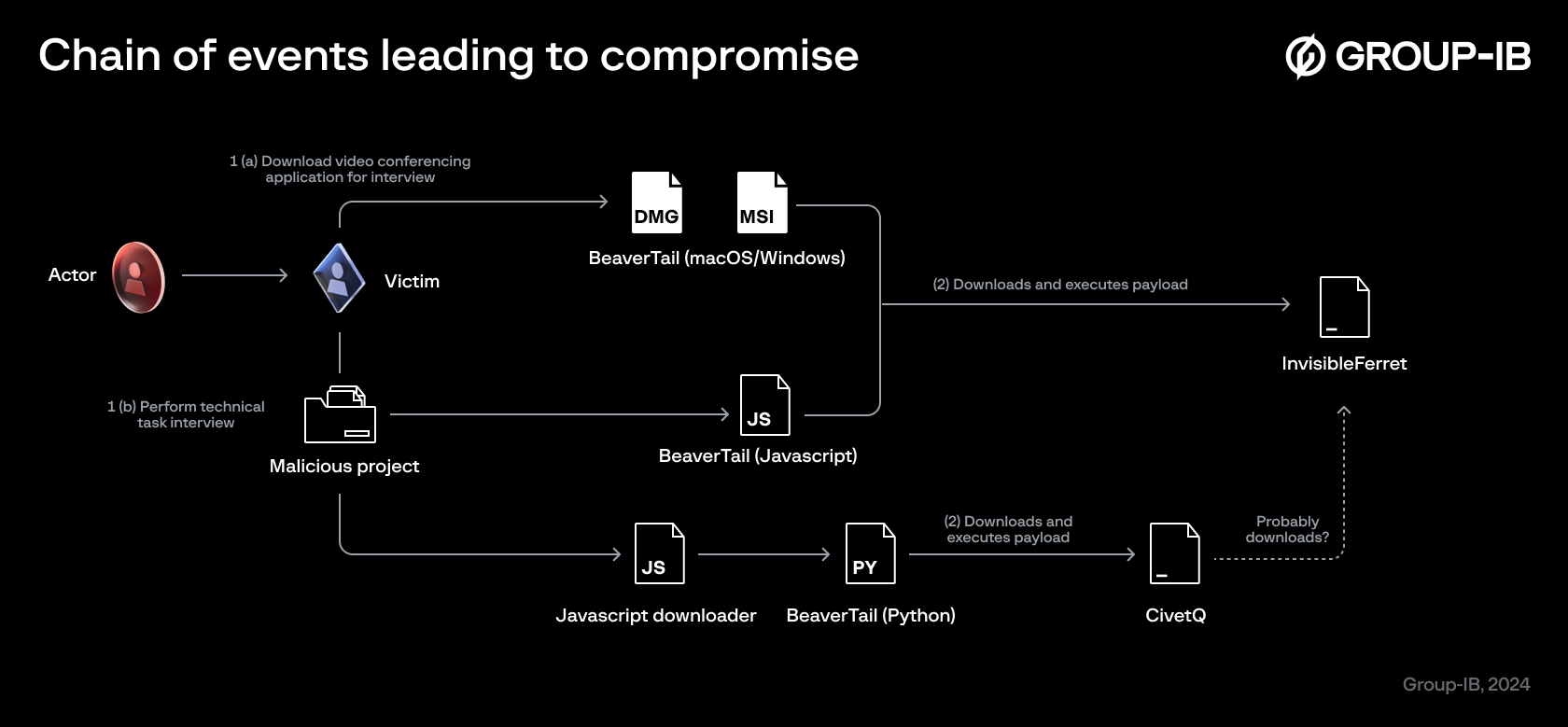
The Lazarus Group continues to aggressively advance its cyber offensive campaign in 2024, employing increasingly sophisticated methods. As part of the “Contagious Interview” operation, the attackers pose as recruiters conducting interviews, embedding malware into the victims’ systems. A critical component of this attack is the deployment of a Node.js-based project, which contains malware called BeaverTail, subsequently installing the Python backdoor, InvisibleFerret.
BeaverTail was first detected in November 2023 as JavaScript-based malware. However, in 2024, researchers uncovered a new variant targeting macOS. Additionally, a fake Windows video conferencing application, disguised as legitimate software, was recently discovered to be part of the BeaverTail attack.
Researchers noted that Lazarus adapts its tools and adds new features to enhance the stealth of its attacks. For example, it was found that the Python version of BeaverTail supports remote access via AnyDesk and is used for data exfiltration through Telegram. The group targets professionals in the blockchain and gaming industries, expanding its attacks on repositories related to cryptocurrency and gaming projects.
There has also been increased use of counterfeit video conferencing apps. One such application, named FCCCall, is a replica of a legitimate service but silently triggers malicious processes upon installation. It harvests data from browsers, cryptocurrency wallet extensions, and password managers, transmitting this information to a remote server controlled by the attackers.
Analysis revealed that Lazarus deploys its tools through code collaboration platforms like GitHub, embedding malicious scripts within legitimate projects. These scripts download core components of BeaverTail, including Python libraries, and a set of scripts researchers have dubbed CivetQ. These tools enable attackers to access browser data, steal information from password managers and cryptocurrency wallets, and maintain control over compromised devices through AnyDesk.
The malware is rapidly evolving, with frequent code updates and the addition of new features such as browser data theft, targeting two-factor authentication applications, and expanding its list of targets to include password managers and Microsoft Sticky Notes.
Lazarus cyberattacks remain a significant threat. Rigorous scrutiny of software and applications before installation, coupled with modern cybersecurity solutions such as antivirus programs and digital risk protection tools, will help mitigate the likelihood of such threats successfully infiltrating systems.


