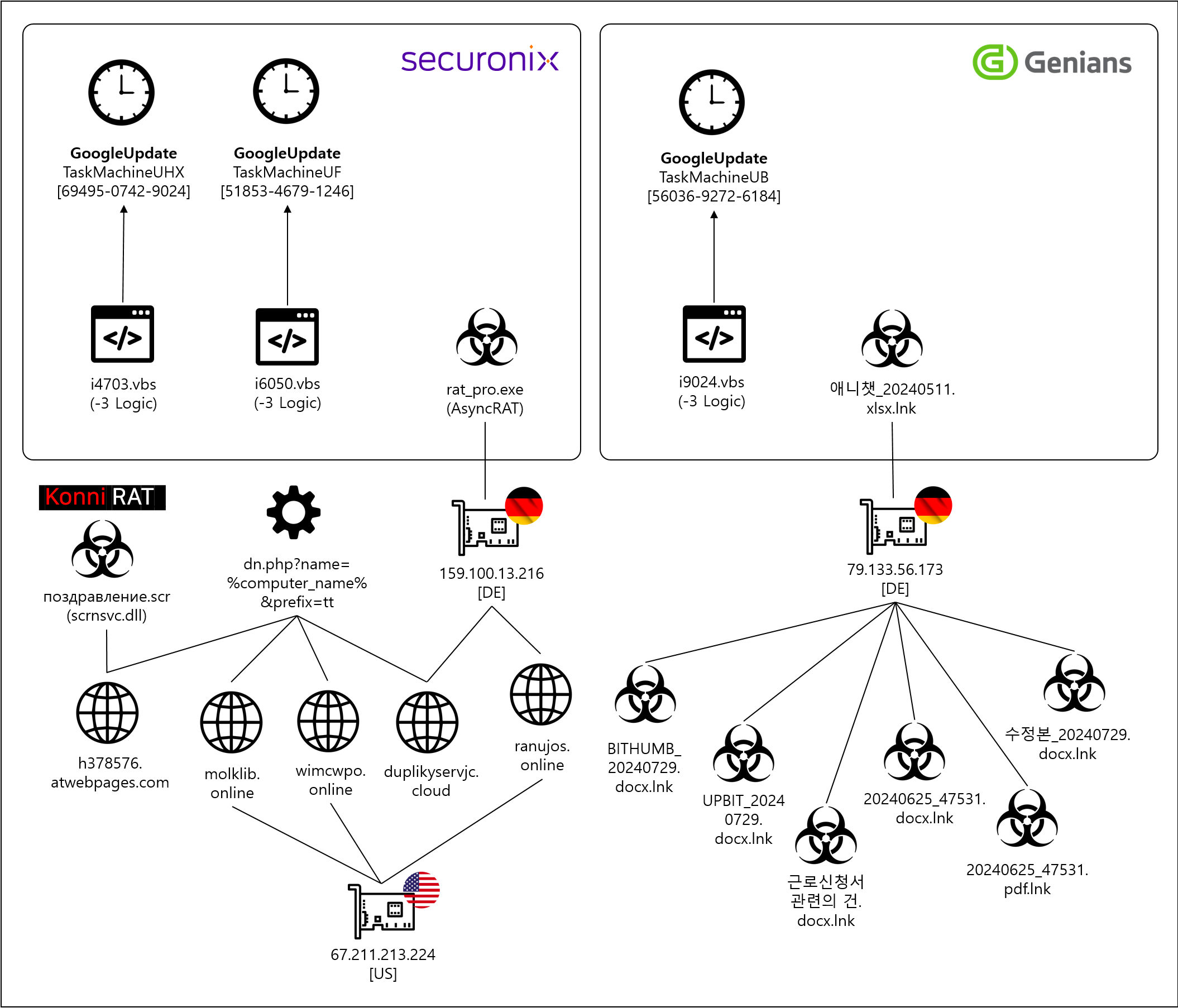
An analysis of the threats linked to the Konni campaign reveals increasing activity by the Kimsuky group, employing a variety of methods for conducting stealthy attacks. The danger lies in their use of legitimate cloud services and FTP for staged infections of target systems, which complicates the detection of malicious files. The campaign not only targets systems in South Korea but also Russian government institutions and other international entities.
By leveraging techniques such as spear-phishing and malicious documents (e.g., files with the extensions `.exe`, `.scr`, `.ppam`), the attackers disguise their assaults as legitimate requests or documents. During one such attack identified in 2022, the adversaries employed fake documents related to Russia’s foreign policy activities, as well as tax and financial operations, underscoring the broad objectives of the campaign.
To execute remote control commands, the attackers utilize free domains and hosting services, facilitating the creation and concealment of command-and-control (C2) servers. A critical aspect of these attacks is the modification and deployment of malware through the creation of remote access trojans (RATs) using PowerShell and VBS, which then execute encrypted commands on compromised devices.
Numerous files uncovered during the analysis showcase the group’s ability to adapt to conditions and employ sophisticated evasion techniques, including both file-based and fileless attacks. Modern Endpoint Detection and Response (EDR) systems enable faster identification of threats and allow for early-stage intervention, reducing the risk of large-scale data breaches.
In recent years, Kimsuky-related campaigns have not only targeted governmental bodies but also individuals involved in cryptocurrency operations, indicating the financial motivations of the group.


