Main function
Black Lotus Labs experts have identified a novel backdoor named J-Magic, which has been actively employed to compromise corporate VPNs running on Junos OS by Juniper Networks. This malicious tool is notable for its advanced stealth capabilities and sophisticated technological design. The backdoor operates through a passive agent mechanism, remaining dormant until it receives a specific trigger—referred to as the “Magic Packet.”
The core functionality of J-Magic involves the covert inspection of incoming network traffic. The malware scrutinizes data packets against five predefined criteria, so precise and subtle that they blend seamlessly with regular network traffic, effectively evading detection by security systems.
Once one of these conditions is met, the backdoor activates, sending an encrypted query to its initiator. Only an attacker possessing a secret RSA key can respond to this query, ensuring the vulnerability remains exclusive to the designated operators and preventing misuse by other hackers.
J-Magic is an evolved iteration of the cd00r proof-of-concept prototype, initially introduced in 2000. However, it surpasses its predecessor by integrating passive monitoring, RSA authentication, and memory-only operation, making it virtually undetectable.
One of J-Magic’s most distinctive features is its ability to exist solely in a device’s memory, bypassing installation on the file system. This approach renders traditional file system analysis techniques ineffective, significantly complicating detection efforts. Additionally, the malware employs SSL to establish reverse connections with the attacker’s IP address, further hindering network traffic analysis and monitoring.
The backdoor has been detected within the networks of 36 organizations spanning industries such as semiconductor manufacturing, energy, IT, and industrial production. The campaign persisted from mid-2023 to mid-2024, though the exact method of J-Magic‘s deployment remains unclear. Potential scenarios include exploiting vulnerabilities in network equipment or leveraging phishing attacks to infiltrate corporate networks.
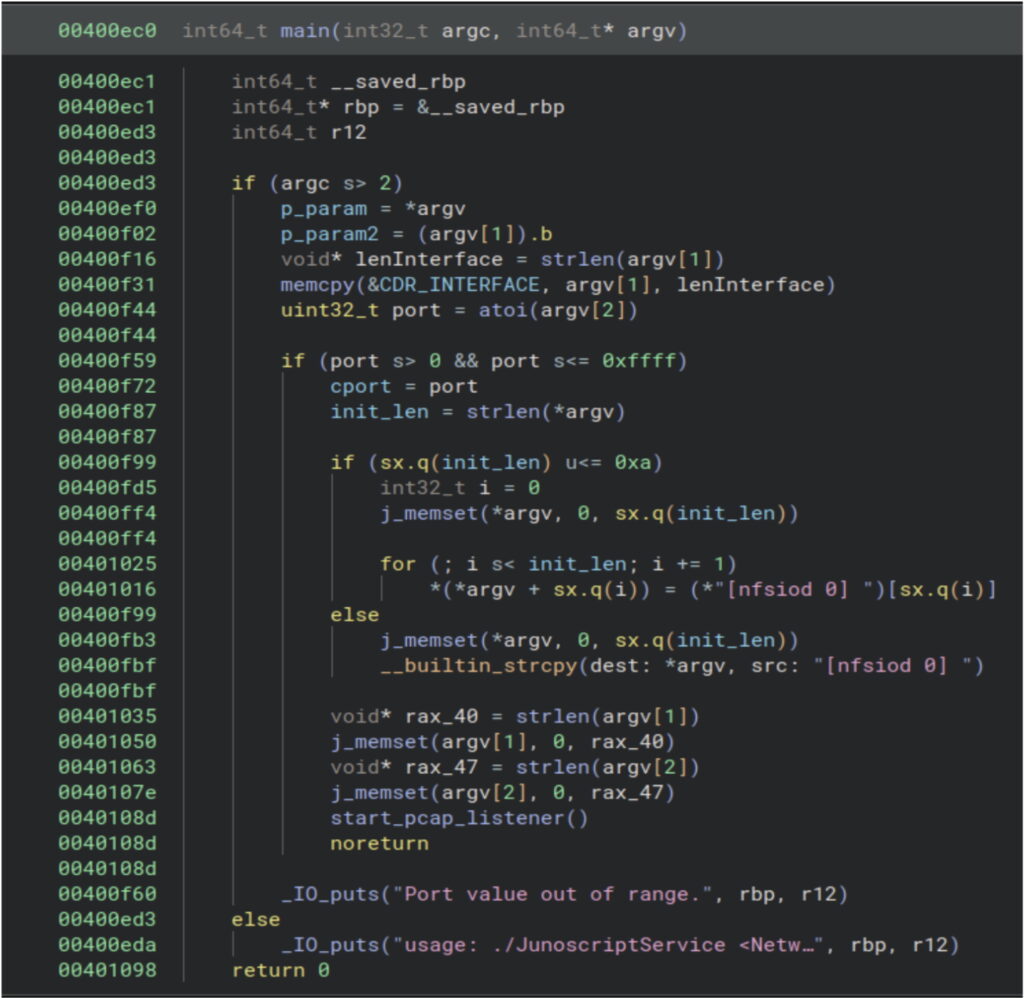
J-Magic activates upon receiving a “Magic Packet” containing specific data. For instance, one condition requires two bytes in a designated TCP header region to equal “1366,” with the destination port set to 443. Other criteria include unique byte sequences and specific configurations of attacker IP addresses and ports within the packet structure. Once any condition is satisfied, J-Magic initiates a reverse connection, encrypting communication using RSA keys.
Following successful verification, the attacker gains command-line access to the device, enabling them to execute arbitrary commands until the session ends.
Experts emphasize that the use of “Magic Packets” significantly enhances the stealth of such attacks. Unlike traditional backdoors that require open listening ports, J-Magic monitors all incoming traffic, leaving no visible traces. This makes it exceedingly difficult for cybersecurity systems to identify active connections associated with malicious activity.
J-Magic exemplifies a broader trend in the use of “Magic Packets” in cyberattacks. A notable parallel is the SeaSpy backdoor campaign, which targeted Barracuda servers. Both pieces of malware operate on FreeBSD, a platform also commonly used by Juniper and Barracuda.
Researchers highlight the urgent need for enhanced traffic monitoring and the development of innovative defensive strategies against such threats. The success of J-Magic underscores the critical importance of addressing both software and network-level aspects of cybersecurity.