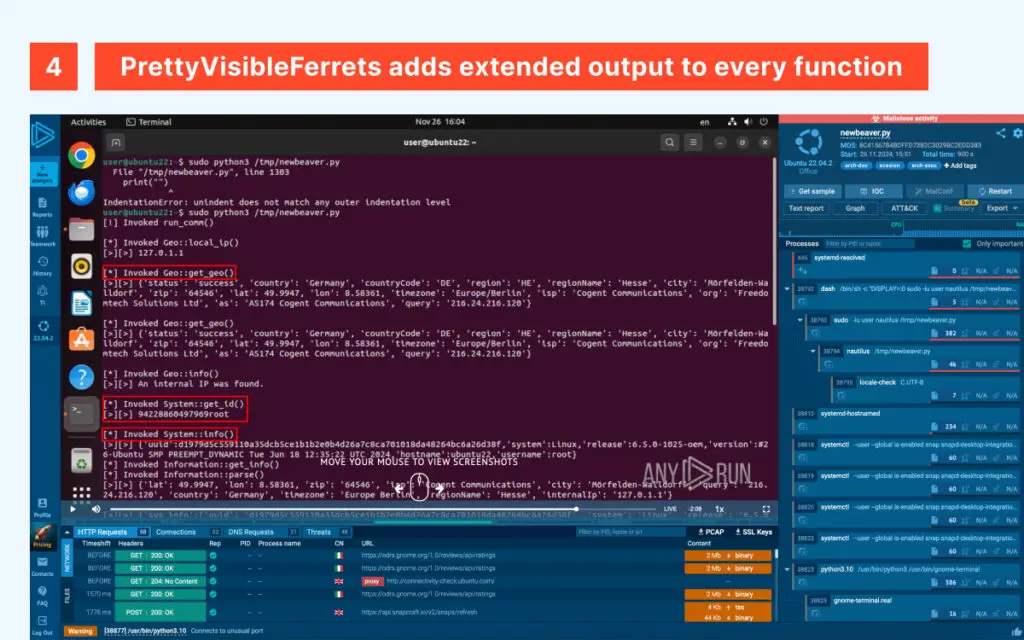
PrettyVisibleFerret running on ANY.RUN showing exfiltrated information in real-time
In October and November, there was a surge in activity from North Korean hackers employing an unconventional method of malware distribution. These threat actors simulate job interview processes to infect victims with malicious programs, such as BeaverTail and InvisibleFerret. Their primary targets are developers working in the technology, financial, and cryptocurrency sectors.
InvisibleFerret is a sophisticated Python-based malware specifically designed to steal source code, cryptocurrency wallets, and sensitive files. Its distribution begins through another malicious module, BeaverTail, which disguises itself as legitimate software dependencies.
InvisibleFerret utilizes services like “ip-api[.]com” to determine the victim’s location and collects details about the operating system, username, and host. The malware then connects to command-and-control servers using uncommon ports, making detection more challenging.
To exfiltrate stolen data, InvisibleFerret employs multiple methods, including uploading files to FTP servers and transmitting them via Telegram bots. The malware is capable of compromising browsers like Chrome, Brave, and Opera, extracting passwords, cookies, and browsing histories. Additionally, it targets extensions for cryptocurrency wallets, password managers, and two-factor authentication applications.
A notable feature of InvisibleFerret is its ability to monitor clipboard changes and intercept keyboard inputs, enabling attackers to steal passwords and other confidential information. Furthermore, it can terminate popular browsers and initiate the next stage of its malicious chain.
Experts at ANY.RUN conducted an in-depth analysis of InvisibleFerret’s behavior, identifying key indicators of compromise. Organized attacks, such as these “fake interview” schemes, require substantial resources, including the creation of realistic attack scenarios. Researchers strongly advise job seekers to verify the authenticity of job offers and avoid running suspicious software.