A new entity has emerged on the horizon of cyberspace—Interlock, a group that has developed ransomware specifically targeting FreeBSD servers. Launched in late September 2024, this campaign has already claimed attacks on six companies, publishing their stolen data after ransom demands went unmet.
Among the victims is Wayne County, Michigan, which was attacked in early October. The first traces of Interlock were uncovered by an incident response specialist known by the alias Simo, who discovered an unusual backdoor during an investigation in October.
Shortly thereafter, the MalwareHuntTeam identified a Linux ELF ransomware sample intended for FreeBSD. Research indicated that the ransomware was built for FreeBSD version 10.4. However, attempts to execute it on a virtual machine proved unsuccessful.
Previously, only groups like Hive had developed ransomware for FreeBSD, but the FBI dismantled its infrastructure in 2023. Last week, Trend Micro reported discovering another ransomware for FreeBSD, along with a sample for Windows. According to their findings, FreeBSD is popular among critical infrastructure systems, making it an attractive target for malicious actors seeking to disrupt organizations and coerce them into paying ransoms.
Interestingly, Interlock has also expanded its operations to Windows, where the ransomware deletes system logs and appends the “.interlock” extension to all encrypted files.
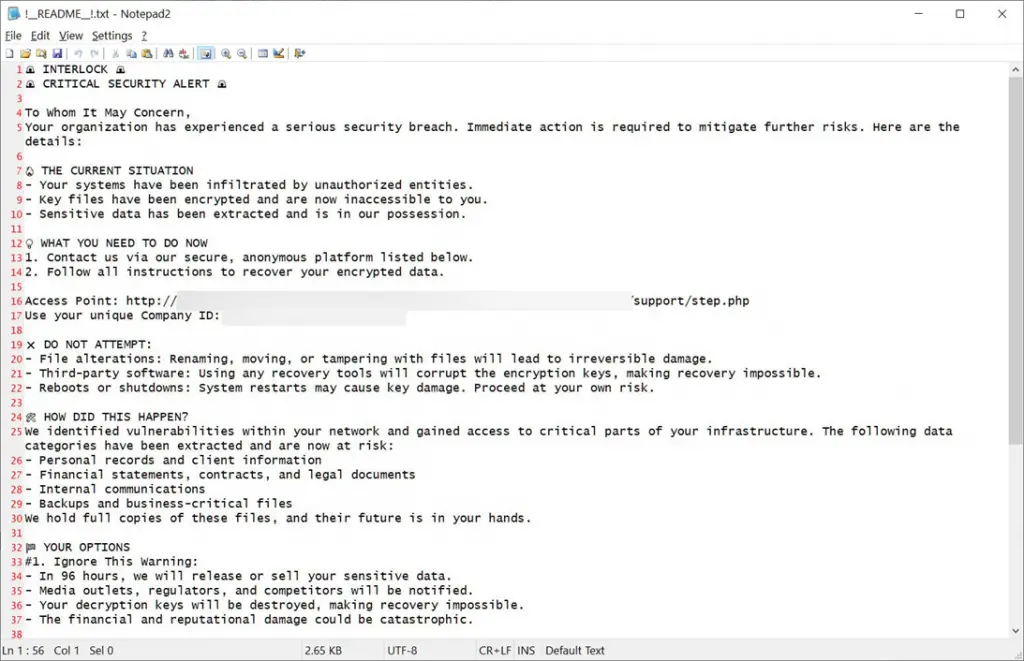
A ransom note is placed in each folder, explaining the fate of the data and providing a link to a Tor site for negotiations.
To increase pressure on victims, Interlock employs a double-extortion technique—stealing data and threatening to leak it if the ransom is not paid. The ransom demands can range from hundreds of thousands to millions of dollars, depending on the size of the organization.


