In August 2024, researchers documented a large-scale DDoS attack targeting gaming platforms that distribute the Chinese game Black Myth: Wukong, including Steam. The operation was meticulously orchestrated and divided into four waves, strategically timed to coincide with peak player activity across various time zones.
The attacks targeted hundreds of servers spread across 13 regions worldwide, maximizing their destructive impact. The operation was carried out using a botnet named AISURU, which later evolved and was rebranded as AIRASHI.
Following the public exposure of the attack in September, AISURU’s activity temporarily ceased. However, by October, the network was upgraded. The new botnet version, initially codenamed “kitty” and later renamed AIRASHI by late November, introduced significant advancements.
AIRASHI is distinguished by several notable features: it exploits a zero-day vulnerability in cnPilot routers for propagation, encrypts strings using RC4, and incorporates HMAC-SHA256 and ChaCha20 into its protocol. Additionally, the botnet possesses formidable attack capabilities and a distributed network of command servers.
AIRASHI actively exploits a wide range of vulnerabilities, including those affecting AVTECH devices, Android ADB Debug Servers, and others. Despite communication with cnPilot’s manufacturer as early as June of the previous year, the vulnerability remains unpatched. To prevent further exploitation, details of the zero-day vulnerability remain undisclosed to this day.
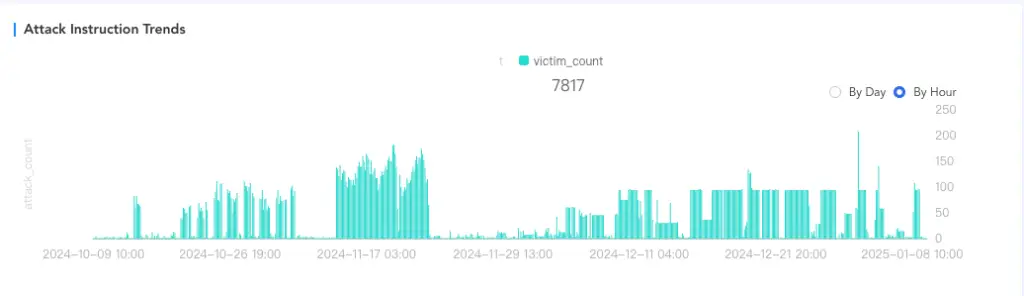
The operators of AIRASHI showcase its capabilities across platforms like Telegram. Performance tests demonstrate a consistent attack peak of 1–3 Tbps, underscoring its devastating potential. Its primary targets include servers in China, the United States, Russia, and Poland, though the botnet indiscriminately attacks hundreds of systems daily.
Technical analysis of AIRASHI samples reveals continuous updates, such as the implementation of SOCKS5 proxies and the integration of new network protocols. The botnet employs advanced encryption techniques, including ChaCha20 and HMAC-SHA256, to secure its communications. Recently, features such as reverse shell capabilities and proxy services have been added, further enhancing its functionality.
Defenders can identify potential attacks through signature-based detection methods designed to recognize exploitation attempts. For instance, Snort rules have been developed to detect commands used by the botnet to execute scripts.
Combatting AIRASHI is complicated by its decentralized structure and ongoing evolution. Nonetheless, cybersecurity experts remain vigilant, monitoring its activity and developing innovative defense mechanisms to counter the ever-evolving threats in the digital landscape.