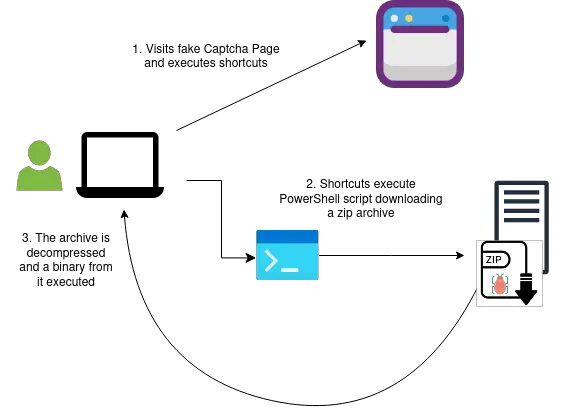
Researchers from the French company HarfangLab have uncovered a new malicious campaign distributing the HijackLoader malware using legitimate digital signing certificates. This malicious activity was first detected in early October, with the primary aim of deploying a data-stealing program called Lumma.
HijackLoader, also known as DOILoader and SHADOWLADDER, first emerged in September 2023. It is propagated through the download of fake files masquerading as pirated software or movies. Recent attack variations direct users to fake CAPTCHA pages, where they are prompted to input and execute a malicious PowerShell command that downloads an infected archive.
HarfangLab has observed three variations of the malicious PowerShell script since mid-September this year. Among them are scripts leveraging “mshta.exe” and “msiexec.exe” to execute code and download malicious data from remote servers.
The archive downloaded by victims contains both a legitimate executable and a malicious DLL that installs the HijackLoader. The malware decrypts and executes encoded data designed to download and launch the infostealer.
Since October 2024, the attackers have started using signed binary files instead of DLLs to evade detection by antivirus software. While it remains unclear whether all the certificates were stolen, experts believe that some may have been generated by the attackers themselves. It has been reported that the certificates used to sign the malware have since been revoked.
SonicWall has also recently reported an increase in attacks targeting Windows systems, this time using the CoreWarrior malware—a trojan that spreads rapidly by creating multiple copies of itself and establishing backdoors for remote access.
The use of legitimate digital signatures to distribute malware demonstrates that even familiar security methods can become powerful tools in the hands of cybercriminals. This underscores the importance of continually advancing cybersecurity measures and maintaining vigilance against any suspicious activity, even if it initially appears safe.


