The GuidePoint Research and Intelligence Team (GRIT) has observed the activities of a highly sophisticated hacking group, possessing advanced skills in social engineering and network infiltration, including proficiency in communicating in English at a native level. This group has launched attacks targeting over 130 American companies across various sectors.
The primary objective of the attackers is to obtain credentials and one-time passwords through social engineering tactics directed at individual employees within organizations. These methods remain undetected by traditional security measures as the attacks occur outside the usual visibility scope—using phone calls to employees’ mobile phones and SMS messages. Without reports from users about such calls and messages, security teams may remain unaware of the breach attempt. The hackers persist in their efforts until they find a vulnerable employee.
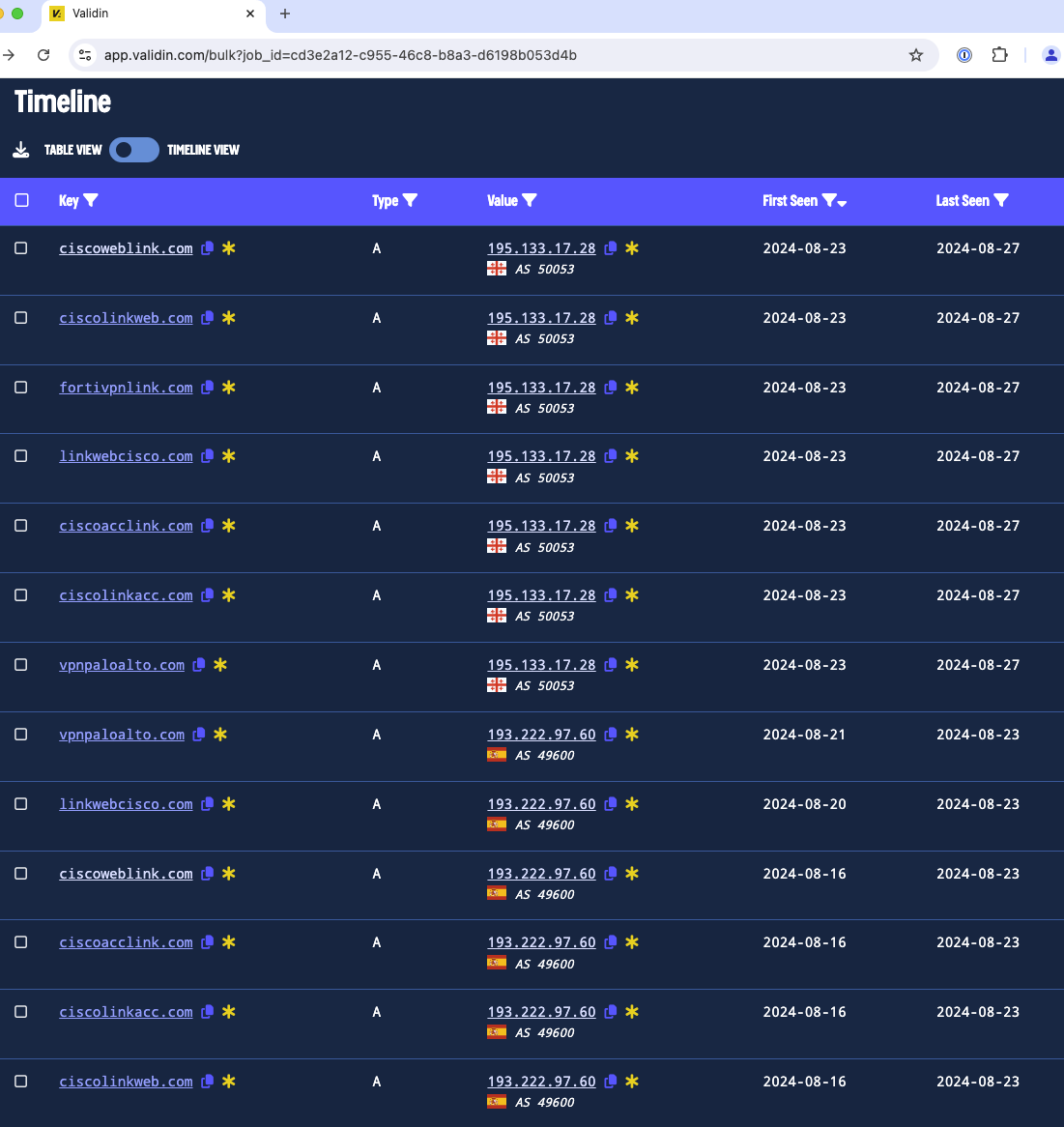
Since June 26, 2024, the group has registered several domain names resembling those used by the targeted organizations’ VPN services. Among them are ciscoweblink.com, ciscolinkweb.com, fortivpnlink.com, and others. The attackers call employees, posing as technical support, and inform them of issues with VPN login, after which they send a link to a fake website. This site mimics the legitimate VPN login page but is designed to steal the user’s credentials.
The fake login pages are meticulously crafted, including the names of the VPN groups used within the organizations. In some cases, fictitious groups like “TestVPN” and “RemoteVPN” are added to enhance the social engineering effect. Through these pages, the hackers obtain the user’s login, password, and, if multifactor authentication is used, the authentication token. If the system uses push notifications, the attackers instruct the user to approve the request to complete the attack.
Upon gaining access to the network via VPN, the hackers immediately begin scanning the network to identify targets for further advancement, persistence, and privilege escalation. The group’s primary aim is financial gain: in the event of a successful breach, they steal data, destroy backups, and ultimately deploy ransomware.
Security teams of companies that may be at risk are strongly advised to review VPN activity logs from the past 30 days for any signs of suspicious behavior. If indicators of compromise are found, an incident should be declared immediately, and a thorough investigation conducted. It is also crucial to inform employees about these new social engineering methods and instruct them to promptly report any suspicious calls from individuals claiming to be IT or support staff.


