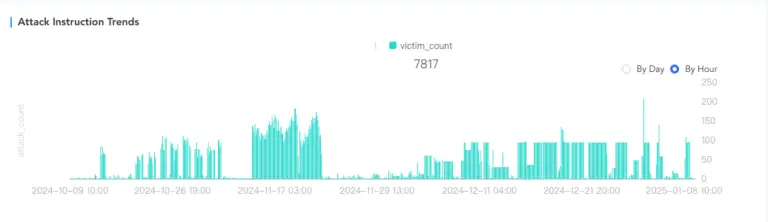
A sophisticated new JavaScript-based attack has been discovered on over 500 government and university websites worldwide. Threat actors have injected malicious scripts that create hidden links within the DOM (Document Object Model), redirecting users to external resources. Although the attack was identified on January 20, 2025, no threat detection systems had flagged the activity as of January 22.
According to the cybersecurity firm c/side, the objective of this campaign is to exploit “black hat” SEO techniques. The malicious links embedded in the code are visually concealed through CSS styling. An example of the applied style is as follows:
style=”overflow: auto; position: absolute; height: 0pt; width: 0pt;”
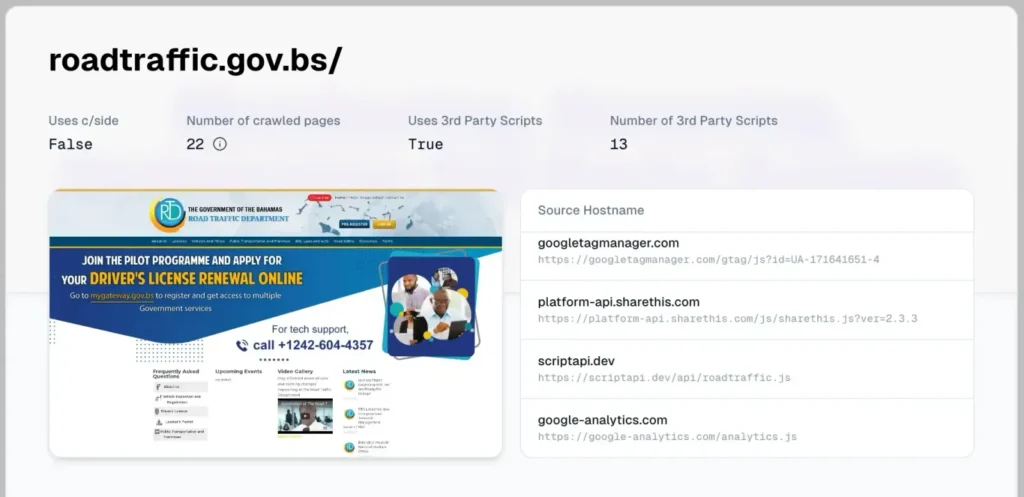
This tactic allows the links to remain invisible to users while being indexed by search engines, thereby boosting the rankings of affiliated resources. The scripts are hosted on the domain scriptapi[.]dev, which features multiple variants, such as:
scriptapi[.]dev/api/smacr[.]jsscriptapi[.]dev/api/en[.]tlu[.]jsscriptapi[.]dev/api/harvardpress[.]js
The script operates by determining its location within the DOM using the document.currentScript method and inserting links before the <script> tag with the insertAdjacentHTML('beforebegin', linksHTML) function.
Affected websites include those leveraging widely used platforms and frameworks such as WordPress 6.7.1, MS ASP.NET, vBulletin, PHP CodeIgniter, and 1C-Bitrix. Comprehensive lists of compromised sites can be found on platforms like PublicWWW and URLScan.
This attack highlights the growing risks associated with the software supply chain in web development. The use of third-party scripts leaves websites vulnerable to such exploits, as these scripts have direct access to the DOM and can execute arbitrary actions within a user’s browser.