In September 2024, researchers at FortiGuard Labs uncovered a sophisticated cyberattack leveraging the SmokeLoader malware against companies in Taiwan. The targeted sectors included manufacturing, healthcare, IT, and other industries. SmokeLoader is renowned for its adaptability, capable of deploying additional malicious payloads or executing complex attacks due to its modular architecture.
The attack began with phishing emails. The perpetrators sent messages containing an attachment disguised as a business proposal. These emails appeared credible, incorporating localized expressions, yet exhibited telltale signs of mass distribution, such as identical recipient names across messages and inconsistencies in the formatting of signatures and contact information.
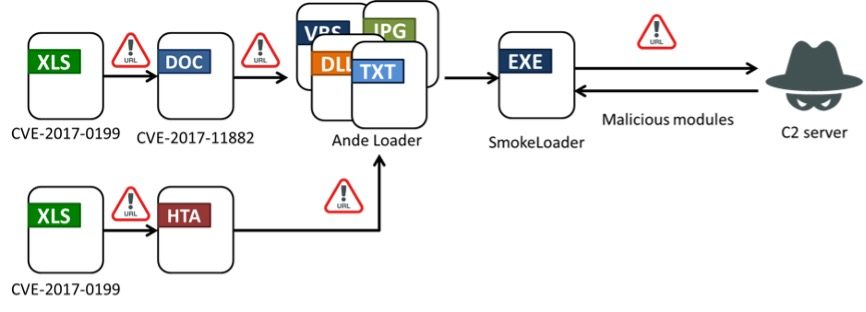
The attackers exploited two vulnerabilities in Microsoft Office to execute the infection. The first, CVE-2017-0199 (CVSS score: 7.8), enabled the automatic download of a malicious file upon opening the document. The second, CVE-2017-11882 (CVSS score: 7.8), allowed attackers to execute code on the victim’s computer via the embedded formula editor. This combination of flaws rendered the attack both highly effective and challenging to detect.
Subsequent stages of the attack involved the use of HTA files embedded with encoded scripts, which decrypted commands and initiated PowerShell to download a new malicious component—AndeLoader. This loader extracted encrypted data embedded within an image file to deploy the core malicious module.
SmokeLoader utilized nine distinct plugins to carry out its operations. Among these were modules designed to steal passwords, browser data, email client information, and FTP credentials. For example, one plugin recorded keystrokes and clipboard data, while another deleted browser cookies, compelling users to re-enter their credentials. The plugins also harvested data from Firefox, Chrome, Outlook, Thunderbird, and FileZilla, transmitting the stolen information to the attackers’ command-and-control server.
Each plugin was tailored for specific tasks. Certain modules were optimized for interacting with browsers, either by erasing data or embedding interceptors to collect sensitive information. Particularly alarming was the malware’s ability to maintain persistence on infected devices. One module ensured automatic execution upon system startup, granting attackers continuous access.
Analysts emphasize that SmokeLoader is a sophisticated tool capable of adapting to diverse attack scenarios. In this instance, it demonstrated how modular approaches can outperform traditional malware. To defend against such threats, Fortinet advises organizations to update their security systems, employ robust antivirus solutions, and train employees to recognize phishing attempts promptly.


