Cybercriminals continue to seek innovative methods to bypass security measures, with one of their latest tactics being the merging of ZIP archives. This approach enables the concealment of malicious files from antivirus software and misleads researchers employing analysis tools.
Perception Point specialists uncovered this technique while examining a phishing email. The email contained a counterfeit delivery notification with an attached archive. At first glance, the archive appeared to be a RAR file, but inside lurked a trojan designed to automate malicious actions.
The essence of this attack lies in creating two or more separate ZIP archives. One contains the malware, while the others are left empty or filled with benign files. These files are then combined into a single archive by appending the binary data of one file to another. The result is a file that appears to be a standard ZIP but, in reality, contains multiple archives within.
Different software applications interpret these directories in varying ways, rendering the malicious files invisible to most antivirus programs. The three most commonly used utilities—7zip, WinRAR, and Windows Explorer—each handle merged ZIP archives differently:
- 7zip: displays only the contents of the first archive and may issue a warning about additional data, which many users ignore.
- WinRAR: shows files from the last central directory, potentially revealing hidden malicious content.
- Windows Explorer: may fail to open the file, display only a portion of its contents, or, if renamed with a .RAR extension, show only the second archive.
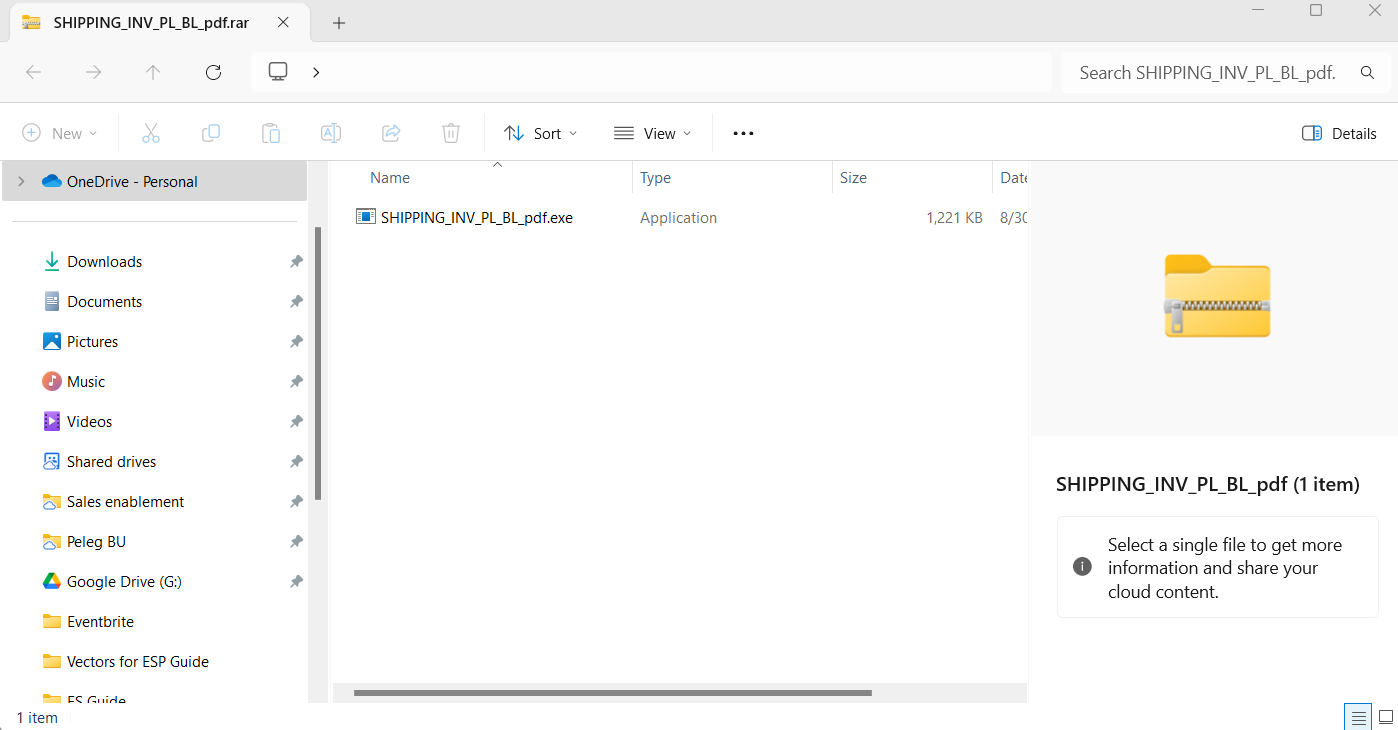
In one incident, cybercriminals sent a trojan disguised as delivery documents. The email contained an attachment titled “SHIPPING_INV_PL_BL_pdf.rar.” Although the .rar extension hinted at an archive, the file was, in fact, a merged ZIP.
When opened in 7zip, only an innocuous PDF document appeared. However, when viewed with WinRAR or Windows Explorer, the malicious files—such as “SHIPPING_INV_PL_BL_pdf.exe”—became immediately visible. The executable was identified as a trojan using AutoIt scripts to automate malicious tasks, such as downloading additional malware.
To protect against such attacks, experts advise employing security systems capable of unpacking nested archives. It is also crucial to exercise caution with emails containing attachments and configure filters to block such files.


