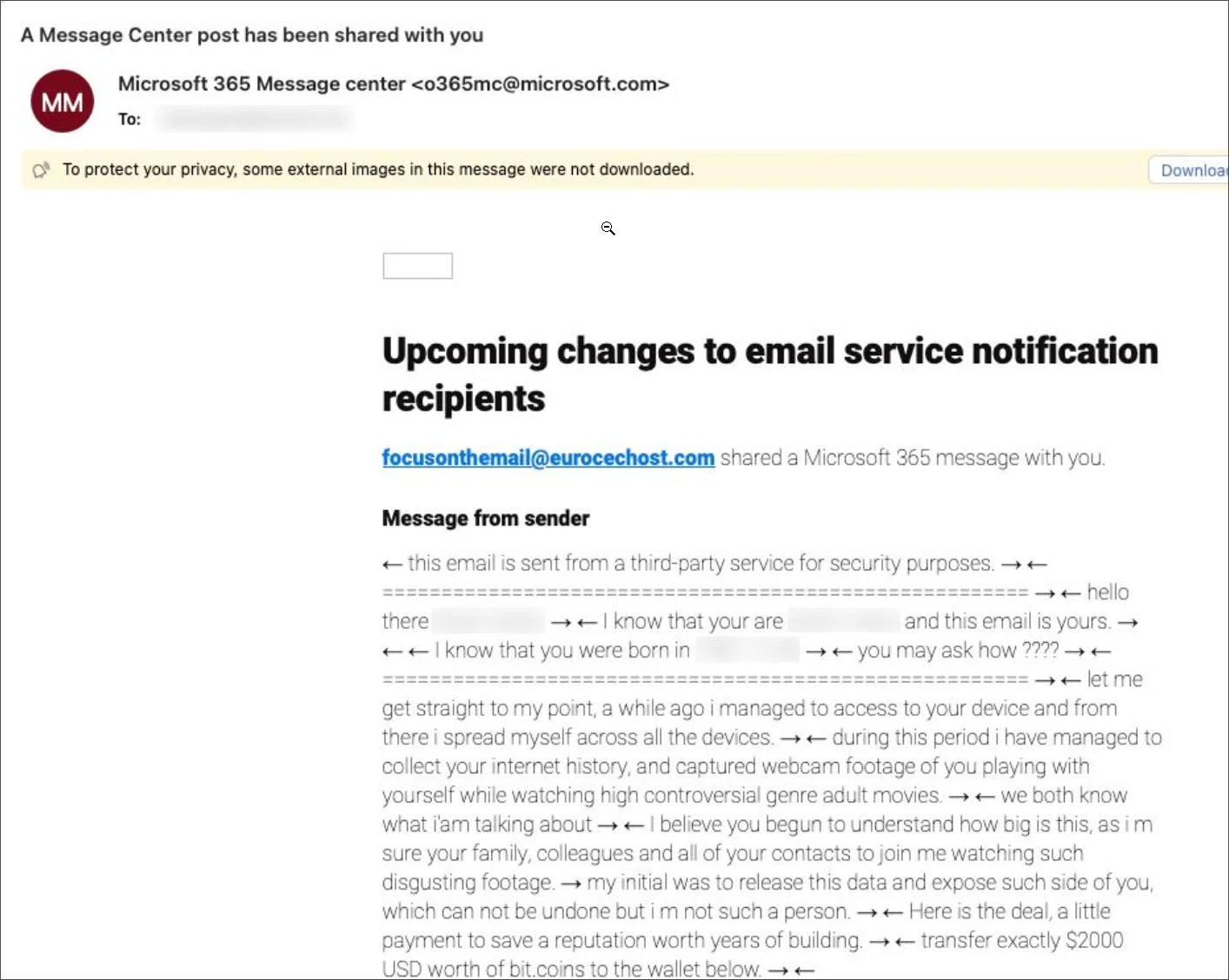
Microsoft has addressed a vulnerability that allowed attackers to exploit the Microsoft 365 administrative portal to send emails containing sexually explicit threats, bypassing spam filters. This scam, which leveraged the fear of disseminating “compromising” materials, stemmed from inadequate data validation on the server side.
The messages were sent from the legitimate address “o365mc@microsoft.com,” enabling them to evade spam detection mechanisms. The attackers utilized the “Personal Message” feature in the Message Center of the Microsoft 365 portal, where administrators share notifications. However, the message field was restricted to 1,000 characters, limiting the length of the text.
The character limit was circumvented by modifying browser parameters. Hackers manually adjusted the maximum allowable character count in the HTML code of the page, enabling the transmission of a complete threat message. Moreover, the process was automated, facilitating large-scale dissemination of such emails.
LinkedIn users shared observations of how these messages bypassed spam filters and appeared in primary inboxes. Microsoft responded promptly to the issue, announcing changes to the feature. Now, the “Share” button redirects users to their email client rather than allowing messages to be sent through the portal.
While these attacks have been rendered less effective, the emails remain convincingly crafted and may still distress individuals unfamiliar with their mechanics. Experts emphasize that such messages pose no threat and should be deleted without interaction.
Microsoft’s swift remediation of this vulnerability underscores the critical importance of continuous monitoring and rapid resolution of security flaws, particularly in systems safeguarding corporate data. This incident highlights the need for stricter server-side validation to prevent similar exploits in the future.


