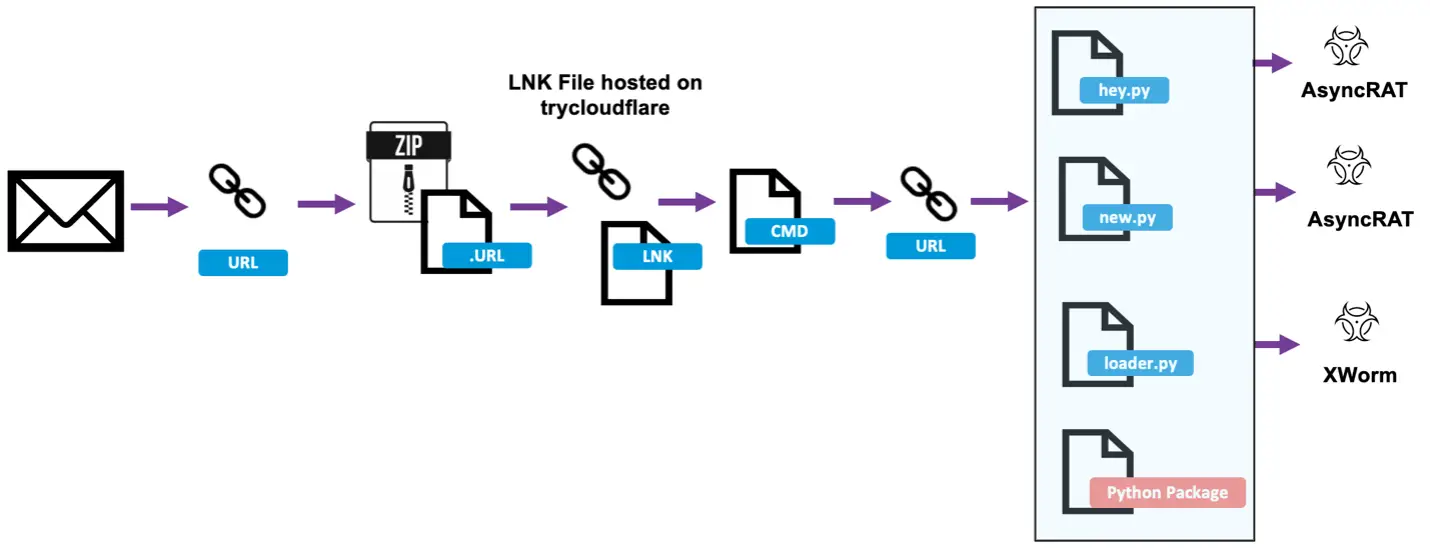
28 May 2024 attack chain
Proofpoint monitors the activities of cybercriminals utilizing Cloudflare Tunnels for disseminating malware. The attackers exploit the TryCloudflare feature, which allows the creation of a one-time tunnel without account registration. These tunnels are intended for remote access to data and resources, akin to VPN or SSH.
The attack chain commences with a phishing message containing a link or attachment leading to a URL file. When opened, the file connects to an external storage via WebDAV to download an LNK or VBS file. Executing these files triggers BAT or CMD scripts that download the Python installer and a series of scripts, culminating in the installation of malware. In some instances, the search-ms protocol is used to retrieve LNK files through WebDAV. Attackers often display a benign PDF to the victim, masking the malicious activity.
Recent campaigns predominantly result in the installation of the Xworm RAT trojan, though previously, AsyncRAT, VenomRAT, GuLoader, and Remcos were also deployed. Some campaigns involve multiple payloads, with each unique Python script leading to different malware installations.
The volume of these phishing emails ranges from hundreds to tens of thousands, impacting numerous organizations globally. These messages are crafted in various languages, including English, French, Spanish, and German, and revolve around business-related themes such as invoices, document requests, parcel deliveries, and taxes.
Despite the consistency of tactics, techniques, and procedures (TTPs) in these campaigns, the attackers continually alter parts of the attack chain to enhance complexity and evade defenses. Initially, scripts were scarcely obfuscated and contained detailed comments on code functionality. However, later iterations show a concerted effort to disguise the code.
Notably, the attack chain requires user interaction to activate the final payload, providing recipients with several opportunities to detect suspicious activity.
The popularity of TryCloudflare Tunnels among cybercriminals surged in 2023. This technology allows attackers to temporarily scale operations, complicating defense and detection efforts. Temporary Cloudflare instances enable criminals to conduct attacks with minimal costs using auxiliary scripts, thereby reducing the likelihood of detection and mitigation.
The use of Python scripts for malware delivery also merits attention. Python library packages and the installer file ensure that malware can be downloaded and executed on hosts where Python was not previously installed. Thus, organizations are advised to restrict Python usage unless it is essential for employees’ work tasks.


