The company GroupGreeting has fallen victim to a cyberattack known as “zqxq.” Malwarebytes experts uncovered an extensive operation resembling previous campaigns involving NDSW/NDSX malware, targeting the popular platform that provides electronic greeting card services.
The scale of the campaign is staggering—more than 2,800 websites have been compromised. These attacks are particularly prevalent during peak user demand periods, such as the holiday season when millions of greetings are sent.
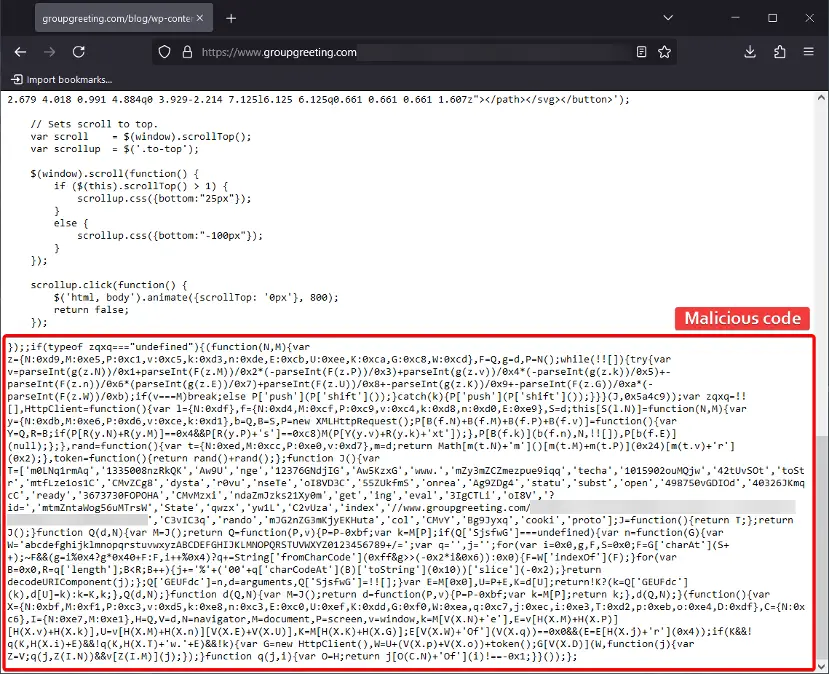
The malware exploits JavaScript, a ubiquitous language on modern web pages. Cybercriminals embedded disguised scripts into critical site components, such as themes and plugins. The malicious code performs multiple functions: generating tokens, redirecting users to external sites, bypassing security measures, and downloading additional malicious elements.
The code’s characteristics, including variable obfuscation and the use of basic decoding functions, reveal striking similarities to other high-profile attacks like NDSW/NDSX and TDS Parrot. These campaigns are distinguished by their stealth and ability to redirect traffic to malicious domains.
Why was GroupGreeting targeted? The platform serves over 25,000 corporate clients, including major companies like Airbnb, Coca-Cola, and eBay. Its high level of trust and increased traffic during the holiday season made it an appealing target for attackers.
Once compromised, user devices were redirected to phishing pages or loaded with additional malware, including data-stealing programs and ransomware.
Experts recommend timely updates to platforms and plugins, implementing file integrity monitoring systems, and increasing user awareness of potential threats to mitigate the risks of similar attacks.


