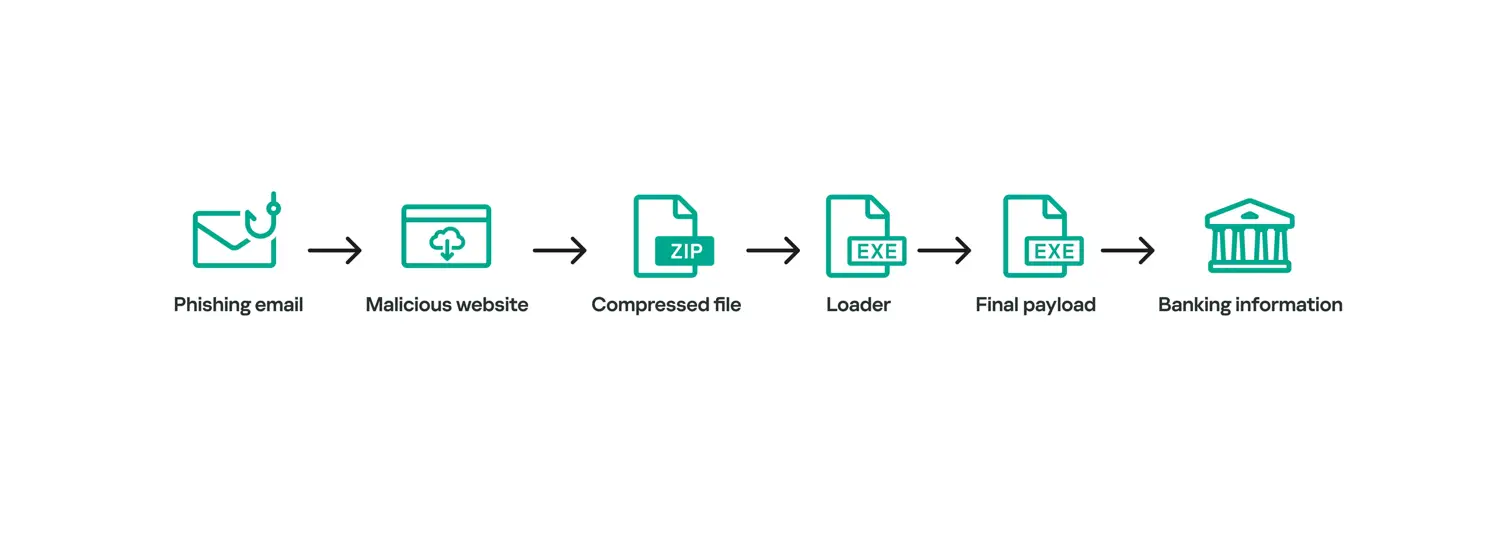
The Grandoreiro Trojan, active since 2016, continues to be utilized by cybercriminal affiliates despite the arrests of its key members in early 2024. According to data from Kaspersky Lab, the latest version of this malware targets clients of approximately 30 Mexican banks, making Mexico one of the most heavily impacted countries by Grandoreiro attacks.
Following a joint operation with Interpol in Brazil, which led to several arrests, Kaspersky Lab experts discovered that the attacks persist. The malicious code has been restructured and broken down into smaller components, indicating that the perpetrators likely still have access to the program’s source material. This has enabled them to launch new campaigns with simplified versions of Grandoreiro.
In addition to the simplified versions, the company’s specialists also identified new techniques employed in the original variant of the Trojan. The malware records and replicates mouse actions, mimicking the real behavior of a user, allowing it to bypass security systems that analyze behavioral anomalies. This method makes the malware more difficult to detect. Furthermore, Grandoreiro utilizes the cryptographic technique Ciphertext Stealing (CTS), which encrypts code strings and significantly complicates its identification. Such a technique has not been previously observed in similar malware.
Grandoreiro attacks remain a serious global threat. In 2024, approximately 5% of all banking Trojan attacks were associated with this malware, with a substantial portion of incidents recorded in Mexico, where over 51,000 users were affected. This year alone, various versions of Grandoreiro have targeted clients of more than 1,700 financial institutions and 276 cryptocurrency wallets across 45 countries.


