The Growing Threat of Weaponized Legitimate Tools
Google is taking proactive measures to strengthen its defenses against sophisticated account takeover attempts following revelations by a U.S. programmer about what he described as “the most intricate phishing scheme” he had ever encountered.
Zach Latta recounted his near miss with cybercriminals, emphasizing that the phishing attempt was so convincingly executed that even he—an experienced user—almost fell for the ruse.
The scammers contacted Latta, posing as representatives from the Google Workspace team. They claimed that an unauthorized login attempt had been detected from Frankfurt and urged him to reset his password as a precautionary measure. The call originated from 650-203-0000, a number commonly associated with automated Google Assistant calls. Even the caller ID displayed “Google,” which immediately lent credibility to the interaction.
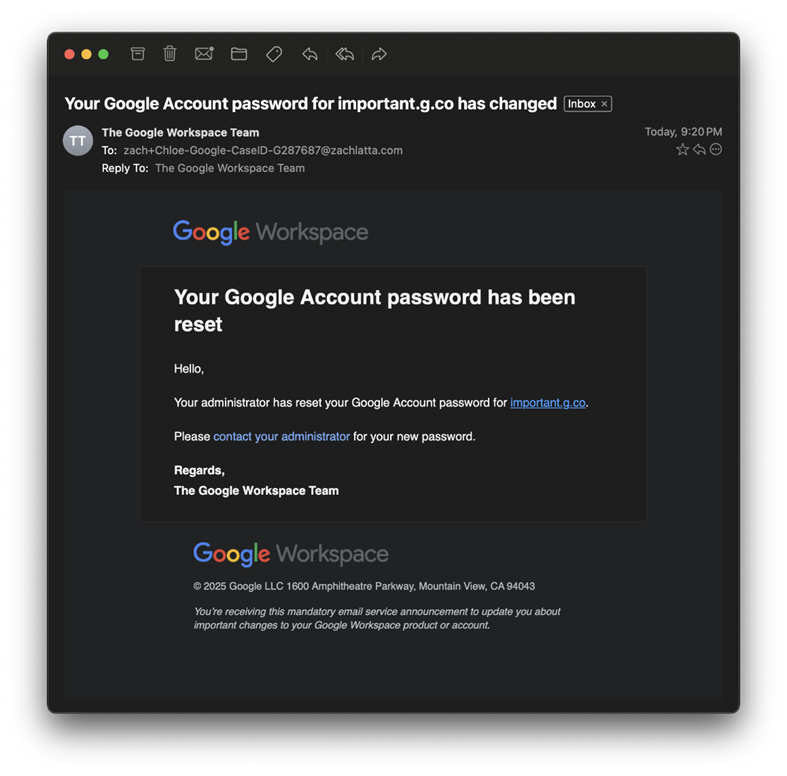
Latta grew suspicious and requested additional verification. The fraudsters, seemingly prepared for such scrutiny, sent an email from workspace-noreply@google.com, an address that appeared entirely legitimate. When Latta proposed calling back via the provided number, an operator, introducing herself as “Chloe,” calmly agreed, further maintaining the illusion of authenticity.
His doubts deepened when another individual, identifying himself as “Solomon,” joined the conversation and provided conflicting information regarding Chloe’s previous instructions. The deception reached its climax when, despite generating a legitimate two-factor authentication (2FA) code that appeared on Latta’s device, Solomon insisted that he press a specific key to confirm the process. This demand proved to be the ultimate red flag—Latta realized unequivocally that he was dealing with fraudsters.
Further analysis revealed that the attackers had leveraged g.co, a legitimate Google-owned subdomain used for creating Workspace accounts and dispatching password reset emails. Exploiting this, the cybercriminals orchestrated the creation of an account under Latta’s name, intending to manipulate him into relinquishing control over his credentials. The use of Google’s own infrastructure made the attack particularly convincing and difficult to detect.
In response to the incident, Google swiftly suspended the fraudulent account used in the attack, emphasizing that such schemes remain relatively uncommon at present. However, the company is enhancing its security mechanisms to prevent similar abuses in the future. A Google representative reiterated that the company never contacts users to request password resets or troubleshoot issues via phone calls, advising individuals to disregard such communications.
Latta’s case is not an isolated incident of voice phishing (vishing). In December 2024, a similar attack was reported in which scammers exploited Google Forms to orchestrate the theft of nearly $500,000 in cryptocurrency.
What makes these schemes particularly insidious is the strategic use of genuine Google services, such as Google Forms and g.co, combined with a deep understanding of multi-factor authentication mechanisms. These techniques are specifically designed to deceive even the most tech-savvy users.
Amid the rising tide of phishing attacks, an increasing number of companies—including Microsoft and Google—are advocating for the adoption of passkeys, a modern authentication technology that provides superior security. As phishing tactics become ever more sophisticated, passkeys are emerging as a robust alternative, offering enhanced protection against credential theft in an era of escalating cyber threats.