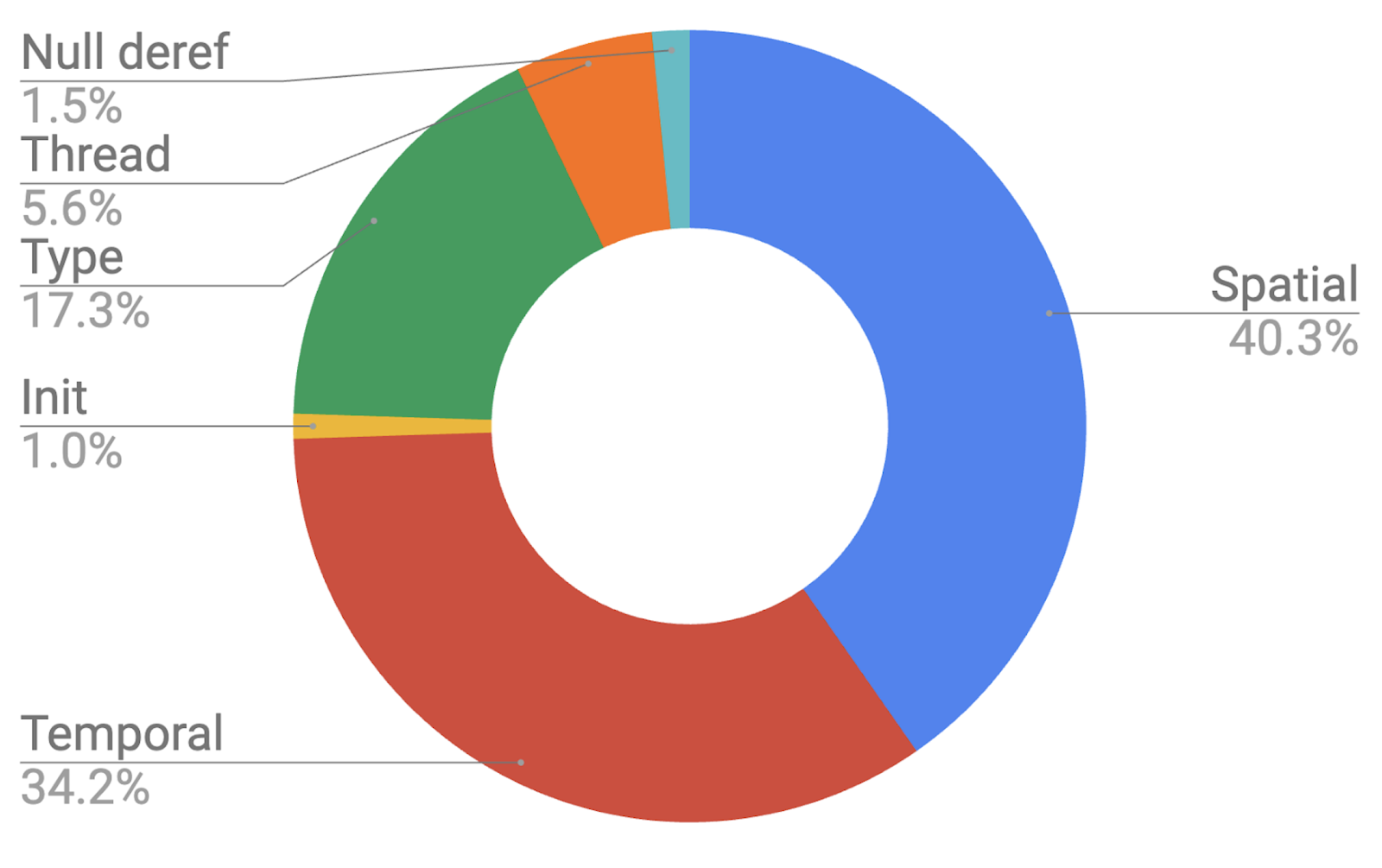
Breakdown of memory safety CVEs exploited in the wild by vulnerability class
Google is actively enhancing the security of its C++ codebase by addressing vulnerabilities related to spatial memory safety. These vulnerabilities occur when code accesses data beyond allocated memory bounds, potentially enabling attackers to compromise systems and exfiltrate sensitive information.
According to Google’s Project Zero, spatial vulnerabilities account for 40% of all exploits observed in the wild over the past decade. To bolster the security of its products, Google is adopting secure coding practices and leveraging memory-safe languages for new code development. However, given the extensive volume of existing C++ code, a complete transition will require several years.
To tackle these issues, Google has begun modifying its C++ codebase using an advanced version of the libc++ library. This update includes boundary checks in standard structures such as `std::vector` and `std::optional`, preventing out-of-bounds access and uninitialized data use.
Initially, these security checks were introduced in the Chrome browser in 2022, and their implementation has since expanded to Google’s server-side systems. Key services, including Search, Gmail, Maps, and YouTube, are now covered. While a small number of critical components temporarily remain outside the new framework, Google is actively working toward a complete transition.
Contrary to concerns about potential performance degradation, boundary checks have caused only a 0.3% slowdown in Google’s services. Through compiler optimizations and profiling techniques, this minimal impact is virtually imperceptible to users.
The migration to the secure version of libc++ followed a three-phase process: testing, adaptation, and gradual deployment in live systems. This initiative has uncovered and resolved over a thousand bugs, reducing system crashes by 30%. Furthermore, these checks have helped prevent several internal attacks and expedited the identification of legacy code errors.
Looking ahead, Google plans to extend these security checks to additional libraries and adopt Safe Buffers to further enhance protection. This approach will streamline interoperability with memory-safe languages and accelerate automated code translation.