The official advertisement for Goissue
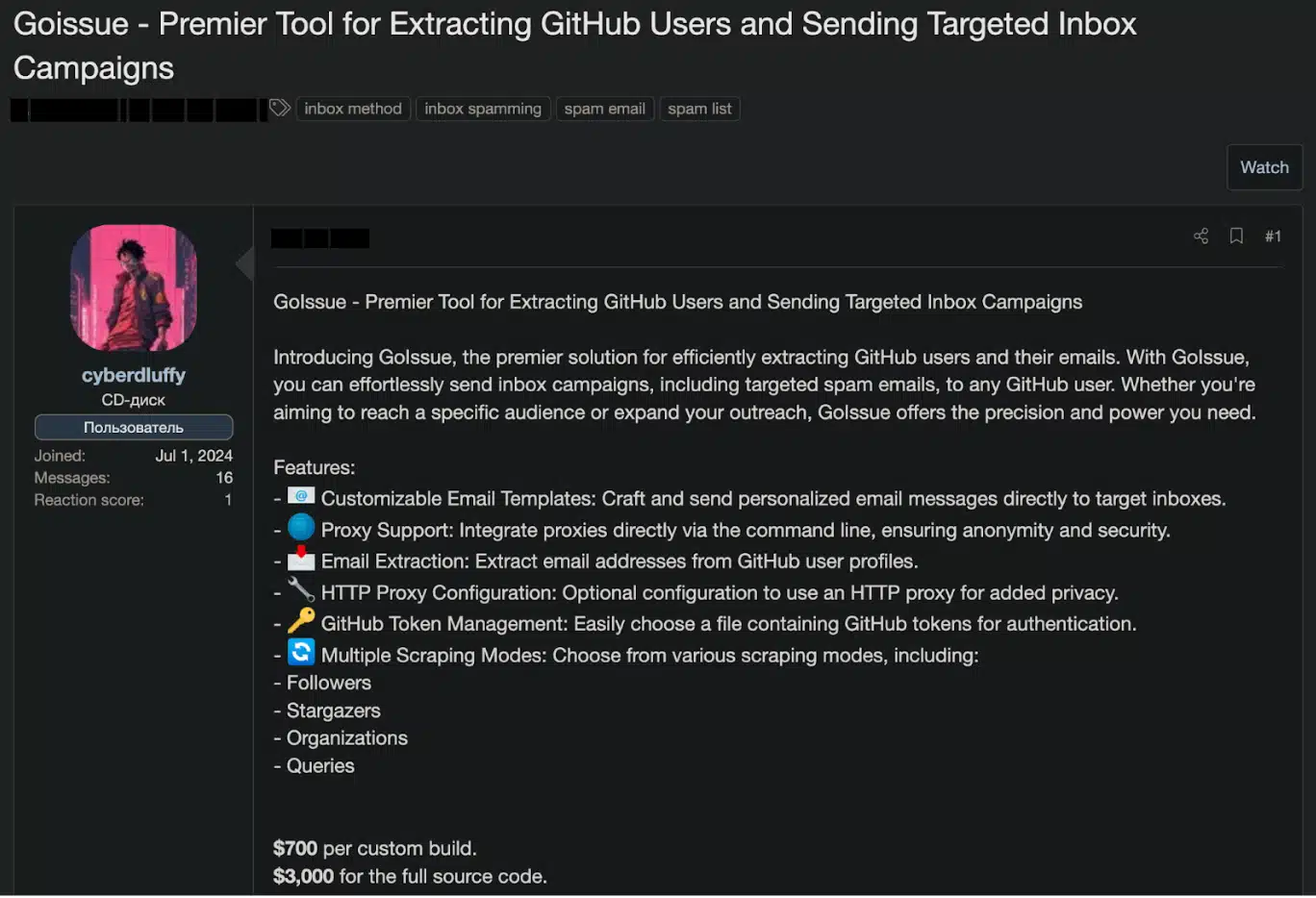
Cybersecurity researchers are sounding the alarm over a new tool, GoIssue, designed for large-scale phishing attacks targeting GitHub users. The tool first surfaced in August 2024 on the Runion forum, advertised by a cybercriminal using the alias cyberdluffy, also known as Cyber D’Luffy.
GoIssue enables attackers to extract email addresses from public GitHub profiles and deliver phishing messages directly to users’ inboxes. According to its creator, the tool targets developers, bypassing spam filters to land directly in their mailboxes.
SlashNext reports that this approach marks a new era of targeted phishing attacks that could lead to source code theft, supply chain compromises, and breaches of corporate networks through developers’ credentials.
GoIssue is available in two versions: a custom build priced at $700 and the source code at $3000. However, as of October 11, 2024, prices were reduced to $150 and $1000 for the first five buyers.
A typical attack scenario involves redirecting victims to fake sites where login credentials are stolen, malware is deployed, or untrustworthy OAuth applications are installed to access private repositories.
cyberdluffy’s profile on Telegram is also noteworthy, where he claims membership in the Gitloker Team—a group previously implicated in ransom attacks on GitHub users. These criminals send links via phishing emails triggered after tagging developer accounts in spam comments, aiming to coerce victims into granting access to private data before deleting all repositories and leaving only a ransom note.
Meanwhile, Perception Point experts, alongside SlashNext, have identified a new two-stage phishing attack using Microsoft Visio (.vsdx) and SharePoint files to steal information. Emails containing collaboration offers are sent from already compromised accounts, allowing them to evade security systems.
When following the email link, the victim is directed to a SharePoint page with an embedded Visio file leading to a fake Microsoft 365 login page. Such multi-layered attacks are increasingly prevalent, exploiting user trust in well-known platforms to bypass conventional security defenses.


