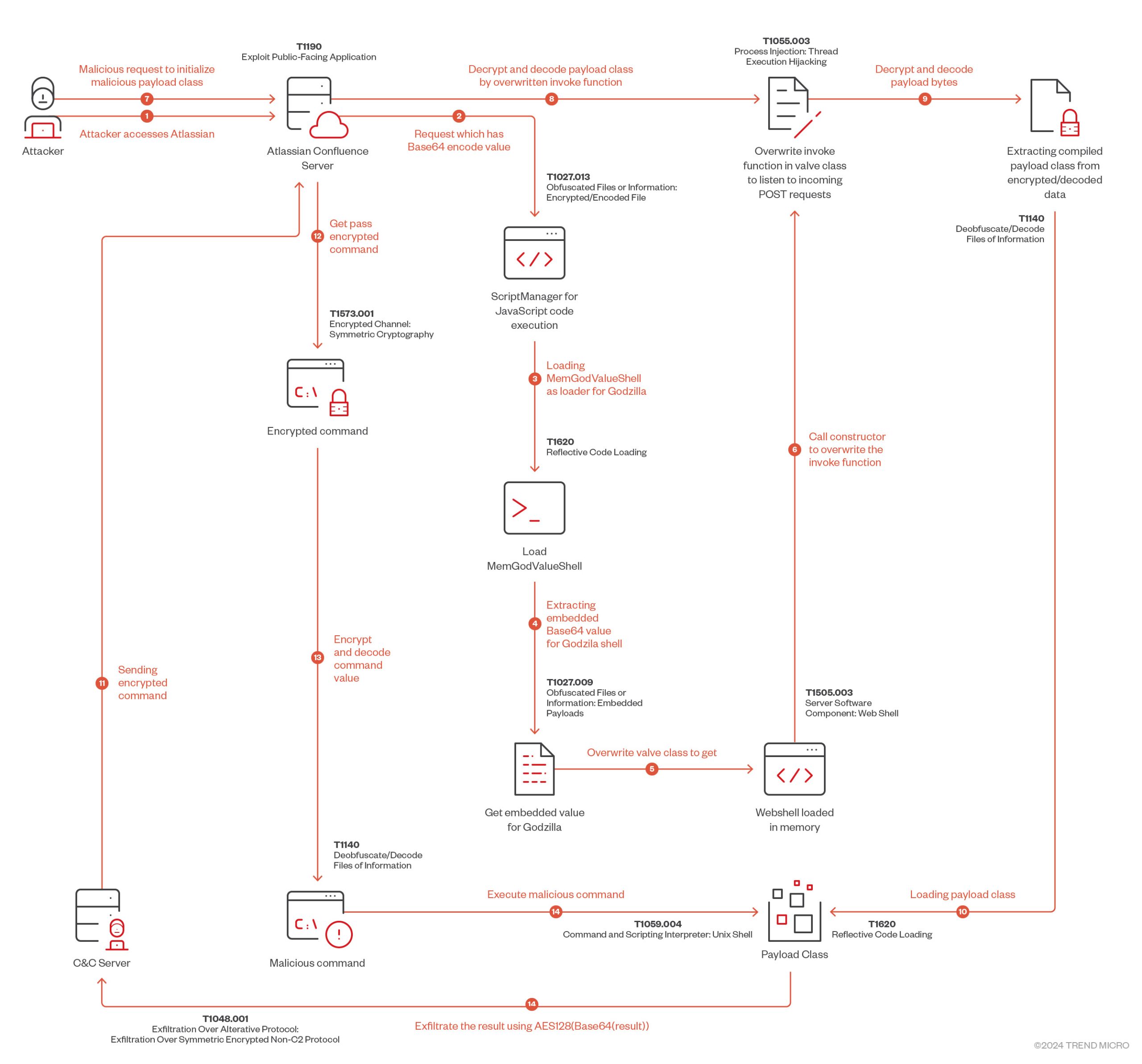
Researchers at Trend Micro have documented the exploitation of vulnerability CVE-2023-22527, which is being used to compromise Atlassian servers by installing the Godzilla backdoor.
The flaw, rated CVSS 10.0, was discovered in Confluence Data Center and Confluence Server products and allows attackers to execute arbitrary code on vulnerable servers, potentially leading to a full system compromise. Although the vulnerability has been patched, it is also being exploited to deploy cryptocurrency miners.
During the investigation of the attack, it was found that attackers uploaded a malicious program to the Atlassian server, which then loaded the Godzilla web shell. This web shell, developed by a Chinese user under the pseudonym “BeichenDream,” is designed to bypass traditional security measures. The primary advantage of Godzilla lies in its use of AES encryption, which significantly complicates detection.
The attack begins by exploiting CVE-2023-22527, through which attackers execute malicious code. Following the initial payload delivery, a complex multi-stage attack chain is initiated, involving the injection of specialized code into the server’s memory. This code allows hackers to embed their own classes and methods, ensuring persistent access to the compromised server.
A distinctive feature of this attack is the use of fileless malware techniques, where the malicious code is executed exclusively in memory, making detection and remediation particularly challenging. Such an attack may go unnoticed if organizations rely on outdated security methods, including signature-based antivirus solutions.
Trend Micro experts emphasize that Atlassian Confluence users must apply patches immediately to prevent potential attacks. It is crucial not only to regularly update software but also to employ modern security solutions capable of detecting and thwarting such attacks.
The Godzilla web shell has been previously observed in other attacks, such as during the exploitation of a vulnerability in Apache ActiveMQ. Godzilla enabled full control over the targeted host, facilitating the execution of arbitrary shell commands, viewing network information, and performing file management operations.


