The Elastic Security Labs team has uncovered a novel technique for distributing the GHOSTPULSE malware — data is now being embedded within the pixels of a PNG file. This method has been hailed as one of the most significant advancements in the malware’s functionality since its inception in 2023.
Previously, GHOSTPULSE (also known as HIJACKLOADER or IDATLOADER) concealed malicious data within the IDAT blocks of PNG files. However, the new algorithm enables the insertion of harmful data directly into the pixel structure of the image, significantly complicating detection efforts.
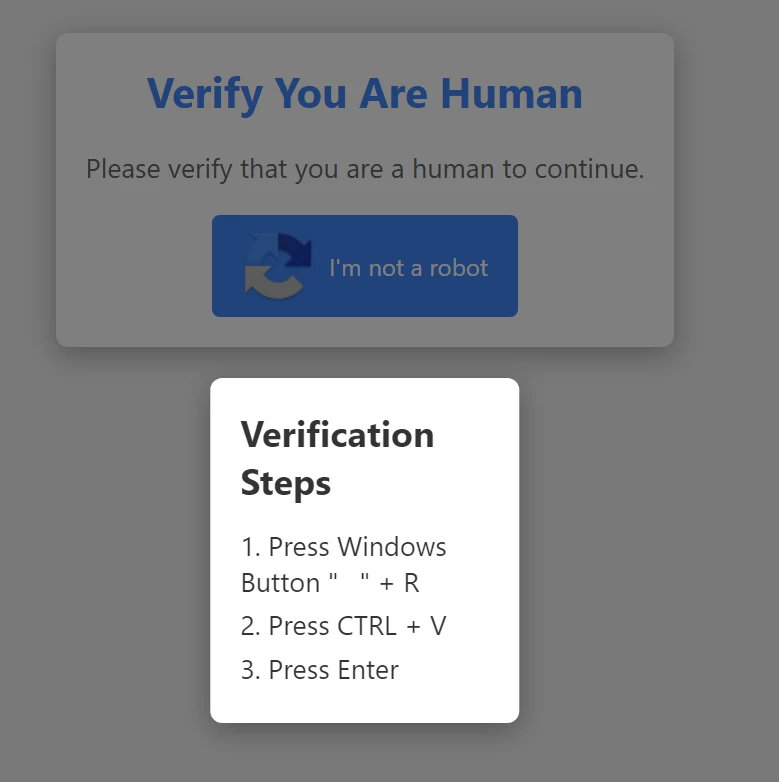
The updated version is already being employed in cyberattacks that leverage sophisticated social engineering tactics. One notable example involves campaigns using LUMMA STEALER, where users are prompted to enter a key combination instead of the usual CAPTCHA, triggering a script that downloads and executes the GHOSTPULSE payload.
In its earlier iterations, the malware was distributed as a package consisting of several files, including an executable, an infected DLL, and a PNG file containing encrypted configuration data. The revised version simplifies the process: a single executable now holds the PNG image within its resource section.
Many of the previous elements, including the Windows API hashing algorithm, remain intact in the new version. However, the primary change lies in the method of configuration retrieval. Instead of relying on the IDAT block, the data is now extracted from the RGB values of the pixels. The program generates a byte array by iterating over each pixel and extracting the color values. It then searches for 16-byte blocks where the first four bytes represent a CRC32 hash, and the remaining 12 bytes contain verification data. A hash match leads to the discovery of the configuration and the XOR key used for decryption.
The latest versions of GHOSTPULSE exhibit a significantly higher level of sophistication compared to earlier ones, which relied on suspicious executable files spread through SEO optimization and advertising campaigns.
These techniques allow GHOSTPULSE to bypass traditional file-based scanners. In light of LUMMA’s growing popularity among cybercriminals, it is crucial to update defense mechanisms. Elastic Security experts have updated YARA rules and a configuration extraction tool to detect and analyze GHOSTPULSE.


