Two years after their last appearance, the Chinese hacker group GhostEmperor has resurfaced. Renowned for their intricate supply chain attacks targeting telecommunications and government entities in Southeast Asia, GhostEmperor has significantly refined their evasion techniques, according to a new report by Sygnia.
Sygnia revealed that GhostEmperor was responsible for an incident late last year, where the network of an unnamed client was compromised and used as a foothold to access another victim’s systems. GhostEmperor was first identified by Kaspersky Lab in 2021. Sygnia noted that the absence of public reports on GhostEmperor during this period remains a mystery.

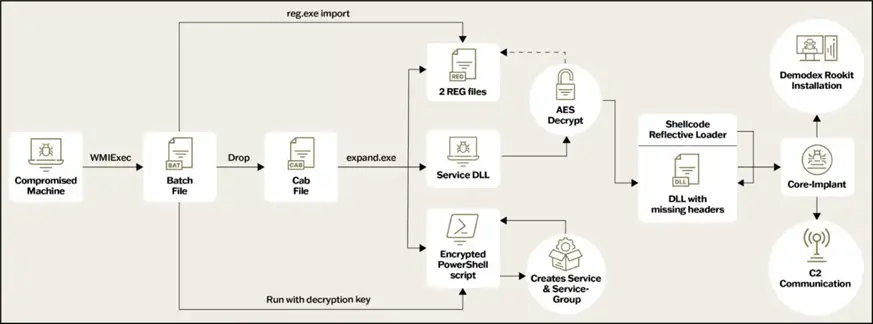
GhostEmperor is known for employing a kernel-level rootkit, enabling it to evade detection by security systems, including EDR solutions. Such tools are typically developed by state-sponsored groups due to the substantial resources required. The rootkit grants access to the privileged part of a computer’s operating system, the kernel, making it extremely difficult for standard security measures to detect.
The Demodex rootkit is primarily an updated variant of its predecessor, but a more sophisticated and covert infection chain has garnered significant interest. This indicates that GhostEmperor continues to evolve their methods to ensure maximum stealth.
In 2021, Kaspersky Lab described GhostEmperor as highly skilled hackers targeting major entities in Malaysia, Thailand, Vietnam, and Indonesia. Additional victims were identified in Egypt, Ethiopia, and Afghanistan. Some organizations in these countries have close ties with Southeast Asian nations, suggesting that the hackers may have used the infections to spy on activities of geopolitical interest to the group.
A crucial aspect of the attack was that after infiltrating a client’s network, the hackers targeted the networks of their business partners. Sygnia hopes that the information provided will help organizations better prepare for such threats. It is essential to minimize the time the adversary spends in the environment and to accelerate the detection process. While 100% security is unattainable, organizations must develop strategies for prevention and risk mitigation.


