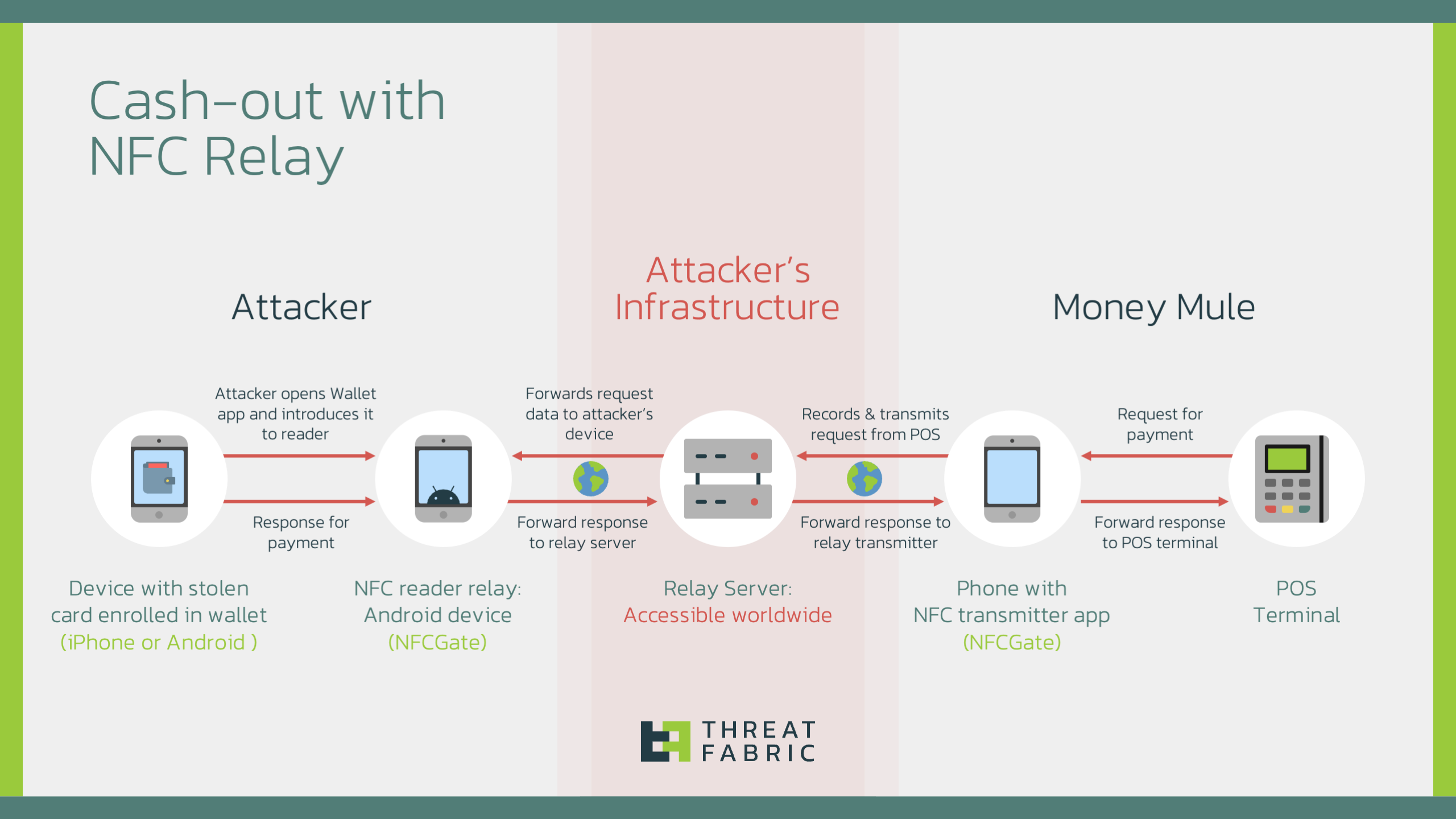
Security researchers from ThreatFabric have uncovered a novel cash-out tactic dubbed “Ghost Tap.” This method enables cybercriminals to exploit NFC technology for anonymous transactions using stolen credit card data linked to mobile payment platforms such as Google Pay and Apple Pay.
The essence of the scheme lies in relaying NFC traffic between devices, allowing transactions to be executed at a significant distance from the card’s actual location. Criminals leverage readily available tools, like NFCGate—originally developed for research purposes—to scale their operations by employing “money mules” to make purchases across various geographic locations within a short timeframe.
To execute Ghost Tap, fraudsters link stolen cards to devices, acquiring OTP codes through phishing websites or mobile malware. The card data is then transferred to the mule’s device, enabling them to carry out in-store purchases. This obfuscates the criminal activity, as the transactions appear to originate from legitimate, single-device operations.
A major challenge for banks and payment systems is the difficulty in detecting these fraudulent activities. The use of airplane mode and low-value transactions bypasses anti-fraud systems. At the same time, criminals can quickly siphon large sums by dividing them into numerous smaller transactions.
The growing prevalence of NFC-based attacks stems from the lack of robust detection mechanisms. To counter such schemes, financial institutions must enhance monitoring systems to flag discrepancies between the device’s and terminal’s locations, as well as unusual customer behaviors.
Ghost Tap vividly illustrates how tools designed for legitimate research can be repurposed into sophisticated fraud mechanisms. Combating such threats requires collaboration between financial organizations, technology developers, and law enforcement agencies. Only through concerted efforts can the evolution of such schemes be effectively curtailed.


