The new malicious software, UULoader, is being actively utilized by hackers to deliver dangerous programs such as Gh0st RAT and Mimikatz. Discovered by researchers at Cyberint, this malware spreads through fake installation files of legitimate applications, targeting users who speak Korean and Chinese.
Researchers have noted that UULoader was likely created by a native Chinese speaker, as evidenced by the presence of Chinese strings in the program database files (PDB) embedded within the DLL file.
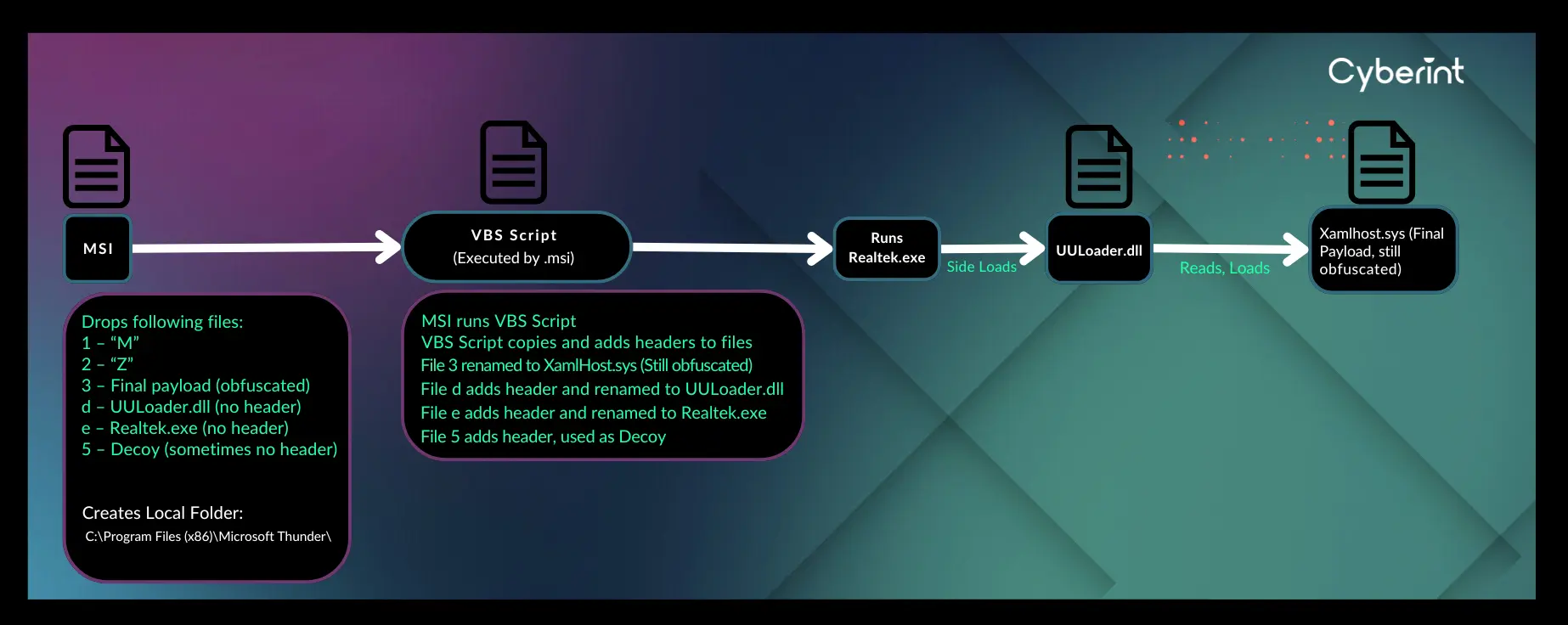
The distinctive feature of UULoader lies in its key files being stored within a Microsoft Cabinet (.cab) archive. The archive contains two executable files (.exe and .dll) with their file headers removed. One of these files is legitimate but vulnerable to the DLL Sideloading method, which allows for the loading of a DLL file that initiates the final stage of the attack.
In the final stage, a disguised file named “XamlHost.sys” is loaded, which is, in reality, a remote access tool. Depending on the hackers’ intentions, this tool could be either Gh0st RAT or Mimikatz.
The installation MSI file also contains a Visual Basic Script (.vbs) that launches an executable file, such as one from Realtek. Some UULoader samples also employ a decoy file to divert the victim’s attention. For instance, if the malware masquerades as a Google Chrome update, the decoy file will be an actual Chrome update.
It is worth noting that fake Google Chrome installation files have been previously used to spread Gh0st RAT. Last month, eSentire reported an attack targeting Chinese Windows users, where a fake Google Chrome website was employed.
The malicious campaign distributing UULoader and similar malware vividly illustrates how cybercriminals continue to refine their deceptive tactics, using legitimate programs to covertly propagate malicious software. It is crucial to remain vigilant when downloading and installing software, especially from unverified sources, as even familiar applications can become tools for hackers to steal data and execute other attacks.


