Intrinsec has unveiled a report on the burgeoning market for the use of Extended Validation (EV) certificates in cybercriminal schemes. The report delves into the methods employed by malicious actors to obtain and exploit these certificates, as well as the threats they pose to security.
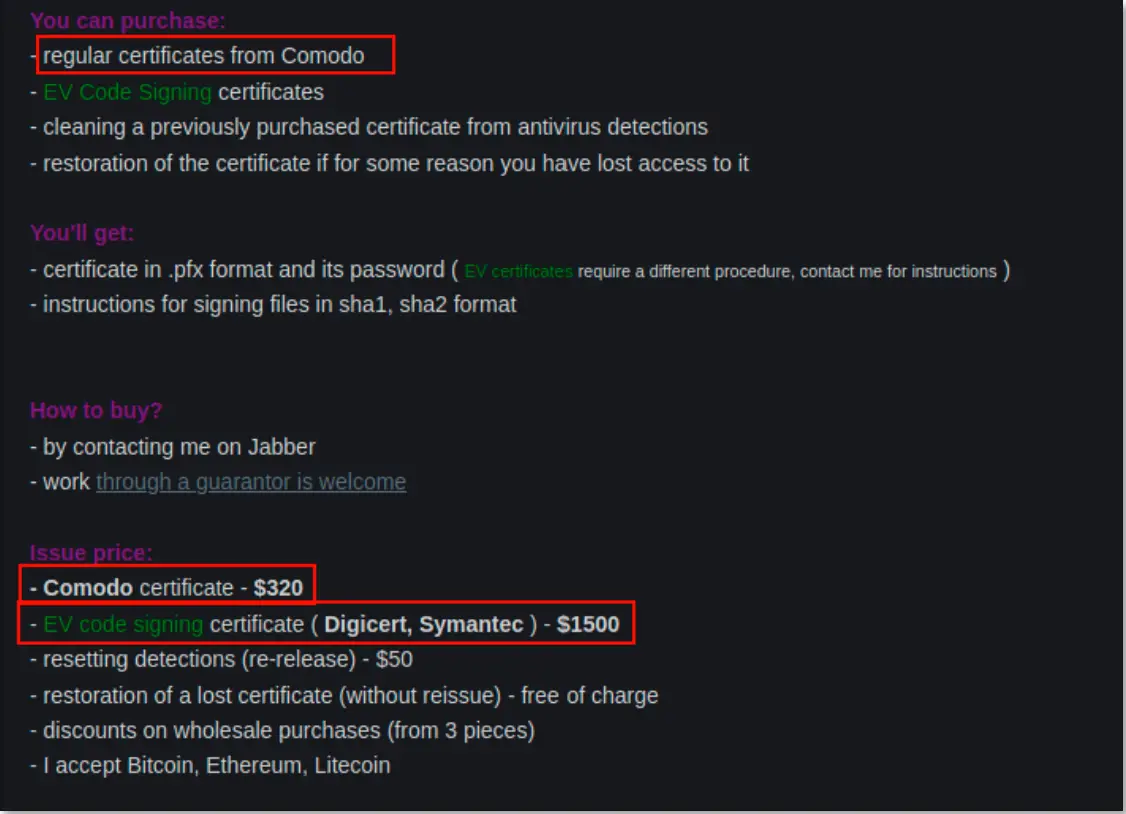
Digital signature technology, originally designed to verify the authenticity and integrity of software, is increasingly being misused by cybercriminals to bypass security measures, gain administrative privileges, and deceive users with seemingly legitimate certificates. EV certificates, in particular, are highly sought after on the black market, with prices ranging from $2,000 to $6,000.
To acquire such certificates, attackers may employ various tactics, including registering new companies, impersonating existing firms, or stealing certificates. The Intrinsec report provides examples of recent attacks where stolen or forged EV certificates were utilized. Notably, malware such as QakBot and Grandoreiro used certificates obtained by impersonating companies or exploiting data from defunct organizations. The report also references an incident involving NVIDIA, whose certificates were stolen by the Lapsus$ group and subsequently used to sign malicious code.
Intrinsec emphasizes that cybercriminals can leverage digital signatures not only to circumvent security mechanisms like Microsoft SmartScreen but also to enhance user trust and reduce the likelihood of detection by antivirus programs.
Moreover, the report highlights services offered on the black market, such as the delivery of physical tokens required for using EV certificates, as well as the provision of remote access to these tokens. Such offerings are disseminated not only on specialized forums but also through messaging platforms like Telegram.
Intrinsec advises organizations to strengthen their certificate authenticity verification processes and implement stricter application management policies. Recommendations also include employee training to recognize potential threats and the use of reputation systems to detect malicious certificates.
This report underscores the necessity of continuous monitoring and adaptation of protective measures to counter the increasingly sophisticated methods employed in cybercrime.


