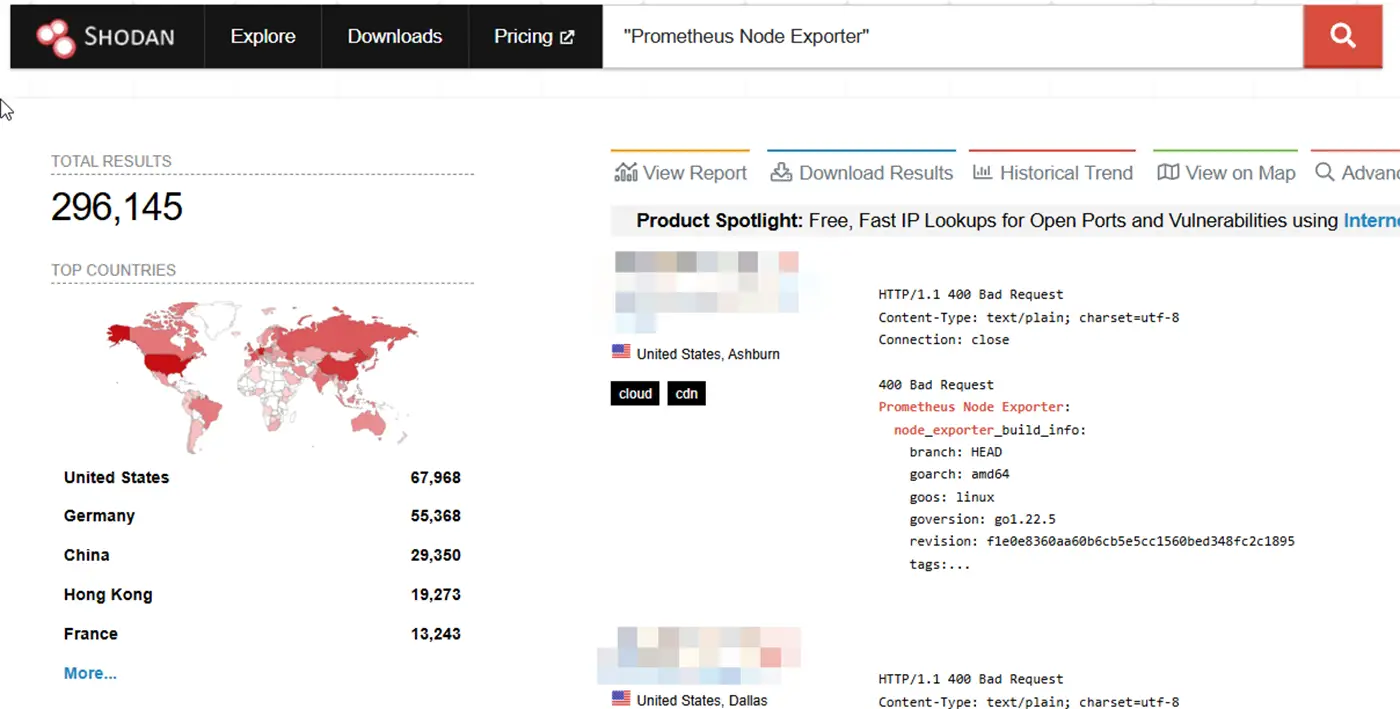
Prometheus exporters in Shodan
Cybersecurity researchers warn of data leakage risks and attacks targeting servers leveraging the Prometheus monitoring tool. According to Aqua Security, hundreds of thousands of Prometheus servers and exporters remain vulnerable to exploitation due to the absence of proper authentication mechanisms.
Analysis reveals that attackers can leverage these servers to access sensitive information, including credentials, authentication tokens, and API keys. Similar issues were identified in 2021 and 2022 by experts from JFrog and Sysdig. Open endpoints, such as “/debug/pprof,” intended for memory and CPU profiling, have also become attack vectors for denial-of-service (DoS) exploits.
It is estimated that approximately 296,000 Prometheus Node Exporters and over 40,000 Prometheus servers are exposed to the internet, presenting a vast attack surface and endangering critical data and services. Moreover, the “/metrics” endpoint divulges information about APIs, subdomains, Docker registries, and other systems, simplifying reconnaissance for malicious actors.
Attackers can initiate a barrage of requests to endpoints like “/debug/pprof/heap,” overwhelming server CPUs and memory, potentially causing system failures. Another significant threat arises from the “RepoJacking” technique, where adversaries hijack the names of deleted or renamed GitHub repositories.
Aqua Security discovered that eight exporters listed in Prometheus’s official documentation were susceptible to such attacks. Threat actors could craft counterfeit versions of these exporters, leading to remote code execution on user systems. Fortunately, these vulnerabilities have since been addressed by the Prometheus security team.
Organizations are urged to fortify Prometheus servers by restricting internet access, implementing authentication, monitoring suspicious activity on endpoints like “/debug/pprof,” and safeguarding against RepoJacking attempts.


