A recent report by Amnesty International has unveiled the use of Israeli-developed software Cellebrite Premium by Serbian authorities to unlawfully hack into the smartphones of journalists and activists. This incident once again highlights the vulnerabilities of modern devices to data extraction threats.
Cellebrite Premium, created by the Israeli firm Cellebrite, has previously been at the center of controversy. In February 2024, it was revealed that the FBI had used the tool to unlock a smartphone linked to a case involving Donald Trump. The device was breached within just 40 minutes, sparking widespread debate.
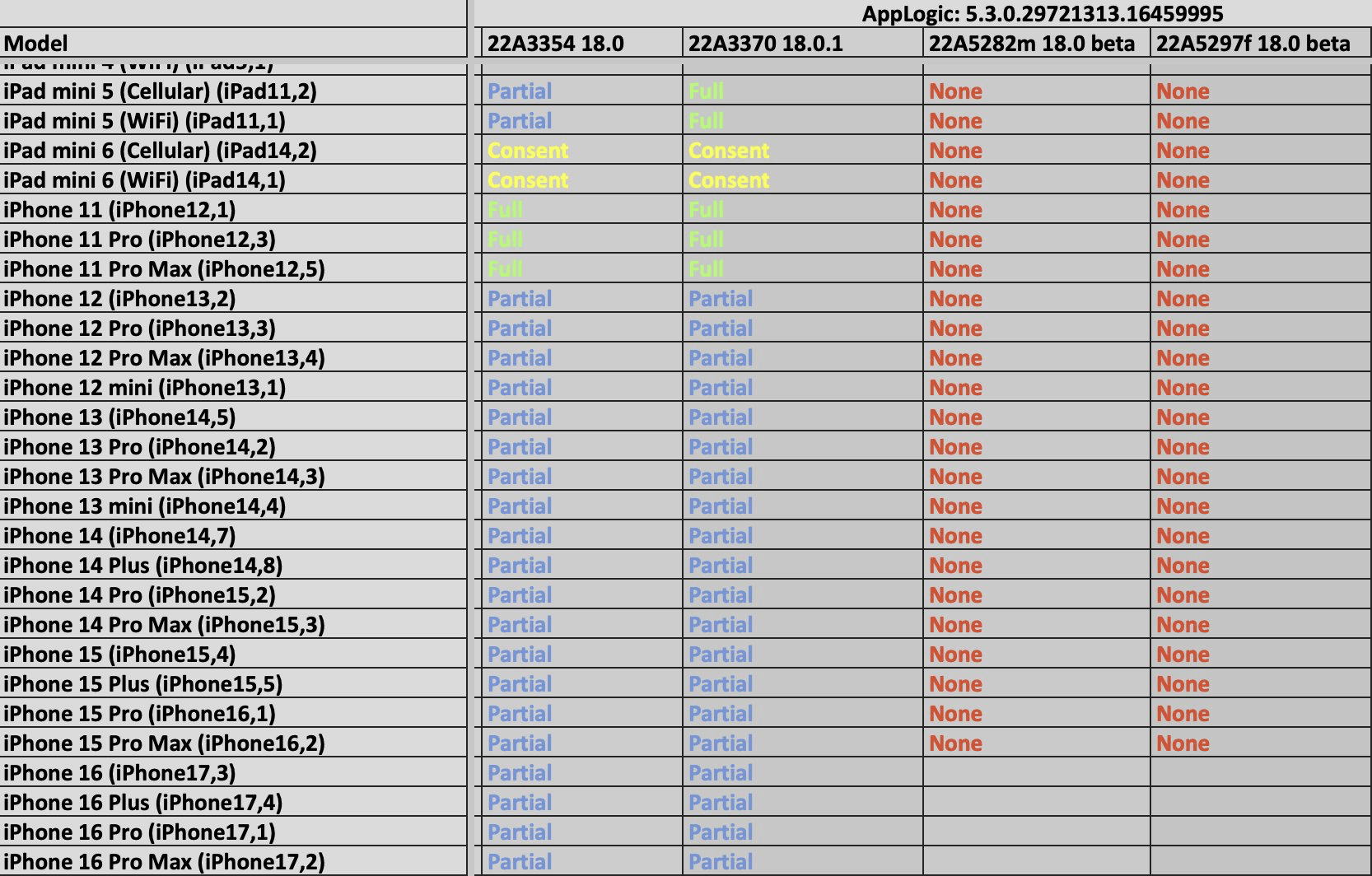
According to Group-IB, once a smartphone is unlocked for the first time, it becomes significantly more susceptible to subsequent attacks. This risk applies to both older models and the latest devices, including the Apple iPhone series (up to the iPhone 15), Google Pixel 8, and Samsung Galaxy S24.
Group-IB’s findings indicate that older devices, such as the iPhone X and earlier models, remain the most vulnerable. However, even modern devices suffer from insufficient protection in AFU (after first unlock) mode, allowing attackers to extract data despite advancements in encryption technologies.
In addition to Cellebrite, other tools pose similar threats. For instance, GrayKey, developed in the U.S., can partially extract data from iPhones running iOS 18 and earlier versions. However, it struggles with the latest iOS updates, limiting its effectiveness.
Beyond software tools, attackers are increasingly employing methods to bypass built-in security features. These techniques include modifying system files, using fake Apple server responses, and circumventing activation locks. Such methods enable not only unauthorized access to devices but also the resale of stolen smartphones as functional units.
The black market has already seen the emergence of price lists for unlocking popular models. These services are often temporary, with access lasting only until the next firmware update. Nevertheless, this timeframe is sufficient for data theft or the resale of compromised devices.
Group-IB underscores that the issue extends beyond device security to the reliability of data extracted from such devices. Given the ease with which data can be manipulated, its admissibility as evidence in court is called into question.
Experts recommend that Apple users activate Lockdown Mode, which restricts access to the device, while Android users are advised to choose models supporting technologies like Memory Tagging Extension (MTE). Manufacturers are urged to enhance the protection of ports and bootloaders to mitigate device vulnerabilities.


