Researchers have uncovered a vulnerability in the aviation security system that allowed unauthorized individuals to bypass airport security checks and gain access to aircraft cockpits.
During their investigation, Ian Carroll and Sam Curry identified a flaw in FlyCASS, a third-party web service used by some airlines to manage the Known Crewmember (KCM) and Cockpit Access Security System (CASS) programs. The KCM program allows pilots and flight attendants to bypass security screening by presenting a barcode or employee number, while the CASS system grants pilots access to the cockpit when they need to travel.
The KCM system, operated by ARINC (a subsidiary of Collins Aerospace), verifies airline employees’ credentials through an online platform. The process involves scanning a barcode or entering an employee number, after which the system cross-references the data with the airline’s database, granting access without the need for security screening. Similarly, the CASS system confirms pilots’ authorization to access the cockpit when required.
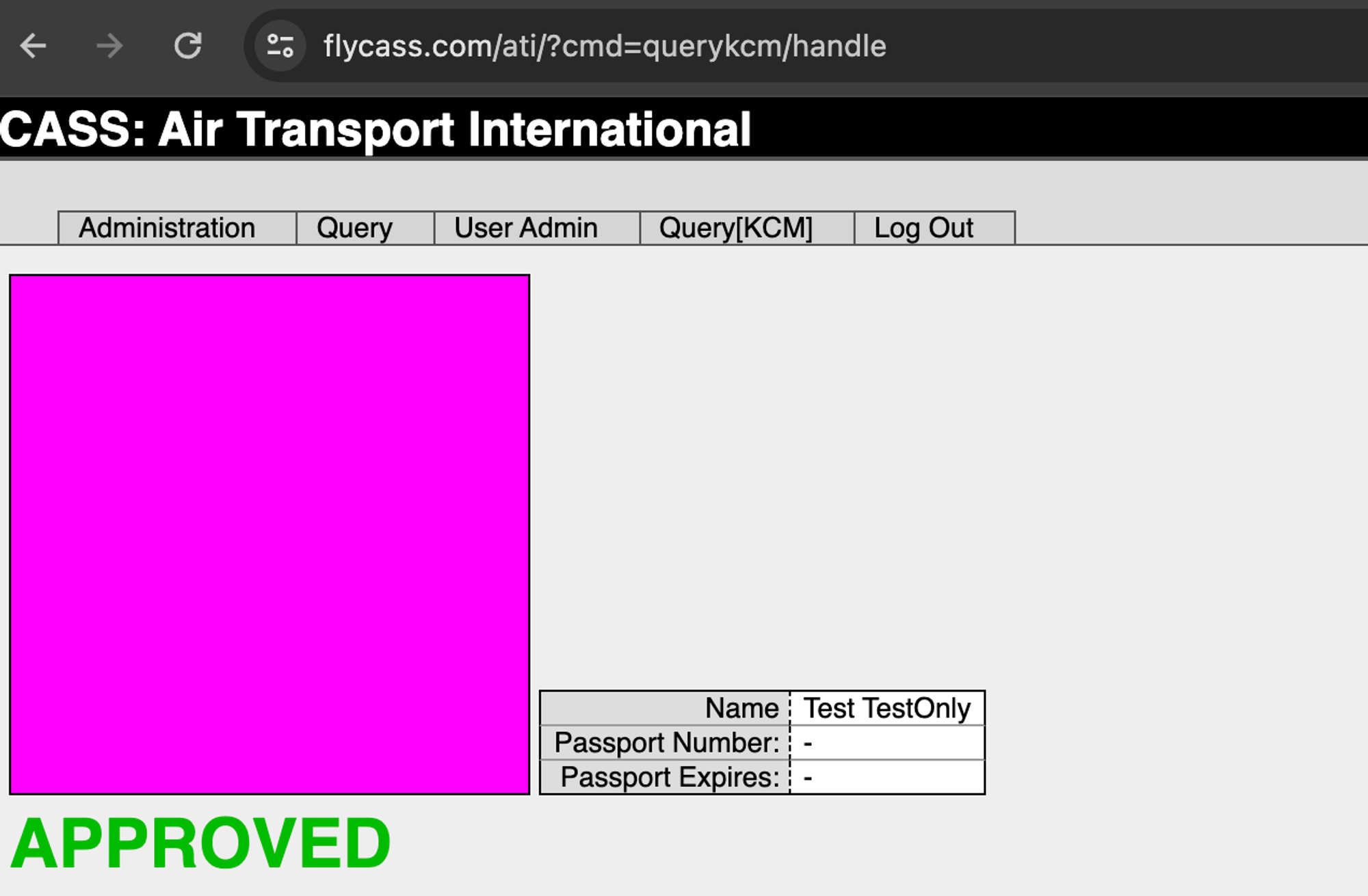
The researchers discovered that the FlyCASS authorization system was vulnerable to a SQL injection attack. This SQL vulnerability allowed the experts to log into the system as an administrator of one of the partner airlines, Air Transport International, and manipulate employee data within the system.
The specialists created a fictitious employee profile named “Test TestOnly” and granted this account access to KCM and CASS, enabling the profile to “bypass security checks and gain access to commercial aircraft cockpits.”
Recognizing the gravity of the vulnerability, the researchers contacted the U.S. Department of Homeland Security (DHS) on April 23. They decided not to contact the FlyCASS website directly, as it appeared to be managed by a single individual, and they feared that revealing the information might alarm the service’s representatives.
The DHS acknowledged the seriousness of the issue and reported that the FlyCASS service was disconnected from the KCM/CASS system as a precautionary measure on May 7. The vulnerability was subsequently patched.
Further attempts to coordinate a secure disclosure of the vulnerability encountered challenges after DHS stopped responding to the researchers’ communications. The Transportation Security Administration (TSA) also issued a statement downplaying the impact of the vulnerability, claiming that the system’s verification process prevented unauthorized access. However, the TSA later removed information from its website that contradicted its statements.
According to Carroll, the vulnerability could have led to more significant security breaches, such as altering existing KCM member profiles to bypass screenings for new participants.
Following the publication of the researchers’ report, expert Alessandro Ortiz discovered that FlyCASS had also been targeted by the MedusaLocker ransomware in February. This was confirmed by Joe Sandbox’s analysis, which revealed encrypted files and a ransom note.
The TSA also stated that no government data or systems were compromised and that there were no consequences for transportation security. The TSA emphasized that it does not rely solely on the database to verify crew members’ identities and that the agency has procedures in place to confirm the identities of employees authorized to access secure areas of airports.


