Jamf, a developer of mobile device management software, has detected a new wave of hacker activity. North Korean threat actors were embedding malware within macOS applications created using an open-source toolkit.
The malicious code was first identified in late October on VirusTotal, a widely used online file analysis tool. Interestingly, despite the malevolent nature of the code, the scanning system flagged the samples as safe.
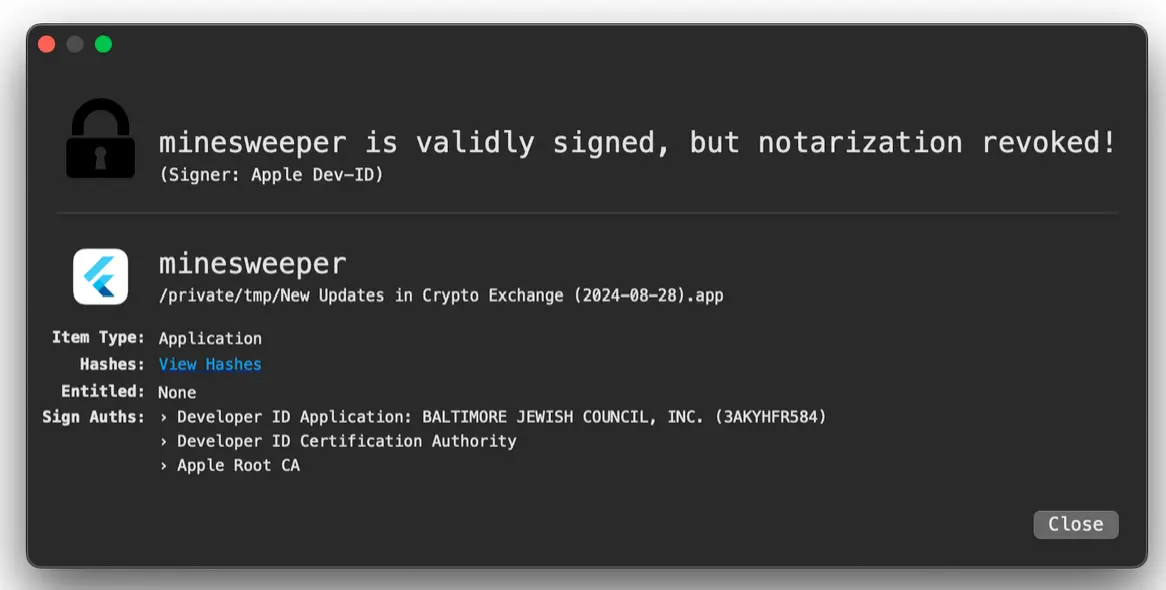
Jamf researchers identified three malware variants: two written in Golang and Python, and a third in Flutter—a framework known for complicating code analysis by default. According to researchers, the techniques and domains linked to the malware bear distinct hallmarks of North Korean hacking campaigns, which are often financially motivated. These campaigns targeted the cryptocurrency sector, utilizing infrastructure similar to that of the North Korean Lazarus group.
Flutter, an open-source framework from Google, enables the development of applications for iOS, Android, Linux, macOS, Windows, and the web. Its architecture significantly complicates reverse-engineering efforts. Jamf experts noted that this feature is not inherently malicious but does facilitate concealing harmful code.
It remains unclear whether the malware was deployed in real attacks or merely for testing new techniques. Nevertheless, the code was sophisticated enough to evade Apple’s security checks for macOS applications.
Specialists discovered the malicious code within a clone of the popular game “Minesweeper,” copied from a GitHub repository. When launched, the program sent a request to a malicious domain intended to trigger the next stage of the attack. However, by the time it was detected, the domain was inactive, returning a 404 error.
Previously, Elastic had reported the use of the same domain in attacks on macOS devices used by blockchain professionals. The North Korean link is further supported by the discovery of a file name in the Go variant of the malware, identical to one found by SentinelOne researchers in a separate macOS operation.


