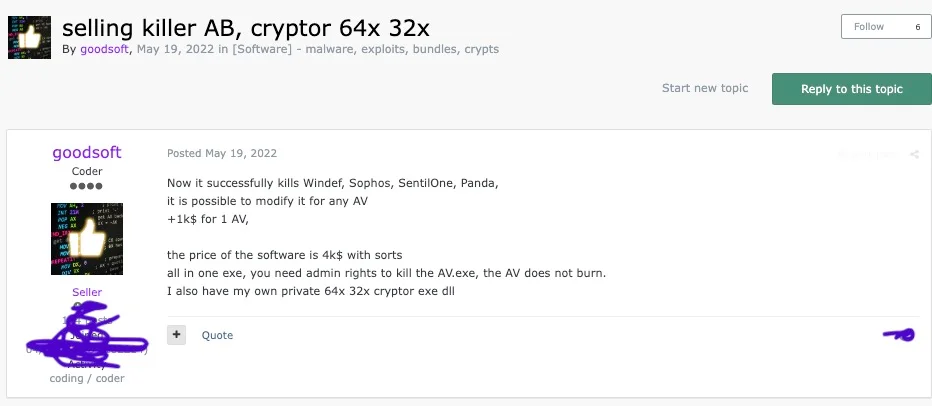
AV killer advertisement by ‘goodsoft’, Google translated from RU
Researchers have uncovered a new fraudulent scheme orchestrated by the notorious hacker group FIN7. The criminals are actively promoting and selling a security evasion tool named AvNeutralizer on dark web forums. This software enables discreet infiltration into victims’ devices, bypassing threat detection systems. According to a recent report by SentinelOne, several ransomware groups have already adopted AvNeutralizer.
The history of AvNeutralizer dates back to April 2022. Interestingly, during its first six months, the tool was utilized by another group—Black Basta—likely one of its initial purchasers.

SentinelOne analysts discovered numerous advertisements on various underground forums promoting the sale of AvNeutralizer. To conceal their tracks, FIN7 employed a variety of pseudonyms, including “goodsoft,” “lefroggy,” “killerAV,” and “Stupor.” The software is priced between $4,000 and $15,000.
A key feature of AvNeutralizer is its customization for each buyer, allowing targeted attacks on specific security systems of their choosing. Since early 2023, the malware has been implicated in numerous cyberattacks, including the deployment of infamous ransomware such as AvosLocker, MedusaLocker, BlackCat, Trigona, and LockBit.
The developers of AvNeutralizer continuously refine their creations. The latest version, detected by SentinelOne, incorporates a new method of security bypass, previously unseen “in the wild.” Specifically, the new version utilizes an embedded Windows driver called “ProcLaunchMon.sys” in conjunction with the Process Explorer driver.
FIN7 has been active since 2013, inflicting significant financial damage on industries such as hospitality, energy, finance, high technology, and retail. Most recently, in April of this year, the group attacked a major U.S. automaker.
SentinelOne experts emphasize that the development and commercialization of tools like AvNeutralizer on criminal underground forums significantly amplifies the group’s impact. The use of multiple pseudonyms and collaboration with other cybercriminal organizations complicate the identification of perpetrators and demonstrate their advanced tactical maneuvers.


