In December 2023, the FBI conducted an operation to dismantle infected systems in the United States controlled by the KV Botnet. This campaign targeted the disruption of infrastructure operated by the Volt Typhoon group, a Chinese-linked entity specializing in attacks on critical infrastructure.
Although a significant number of infected devices were neutralized, the primary command-and-control infrastructure of the botnet remained intact, likely a deliberate strategy to provoke a response from the administrators.
The KV Botnet is a global network of compromised routers and firewall devices used in small office and home office (SOHO) environments. Some of these devices have been exploited by Chinese state-backed hackers to facilitate covert data exfiltration. In late January 2024, the U.S. government announced a large-scale operation to dismantle the KV cluster. Following these efforts, the FBI’s actions also disrupted the JDY cluster, which ceased activity for approximately two weeks.
The KV Botnet exhibits remarkable resilience, enduring repeated attempts at neutralization by researchers and law enforcement agencies. Its operators have merely switched hosting providers, leaving the network’s architecture largely unaltered. This approach starkly contrasts with the technical sophistication Volt Typhoon demonstrates in its targeted organizational attacks, raising questions about the group’s actual role in managing the botnet.
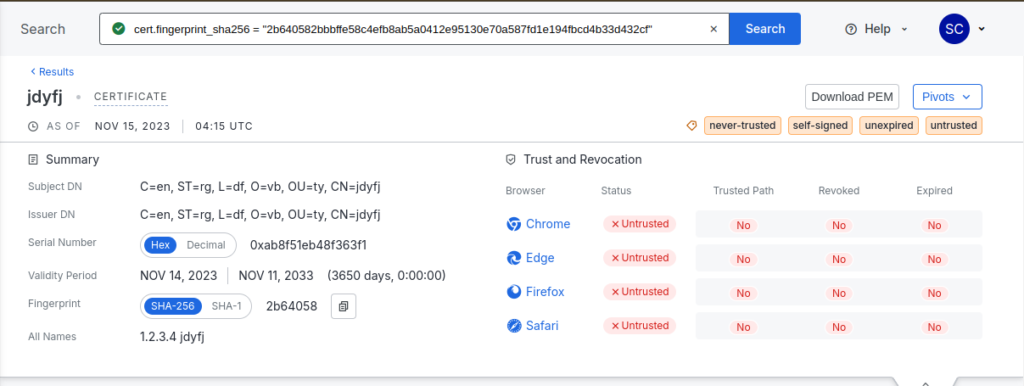
Specialists have traced the botnet’s activity, particularly the so-called JDY cluster, first documented in 2023. This cluster exploits vulnerabilities in Cisco RV320 and RV325 routers to propagate malware. In mid-November 2023, infected devices began connecting to new command-and-control (C2) servers employing an updated certificate signed with “jdyfj.” This certificate enabled researchers to identify several IP addresses used for command operations.
C2 servers at IP addresses 45.32.174[.]131 and 45.63.60[.]39 became active after the FBI’s intervention, supporting the hypothesis that botnet administrators are taking minimal measures to restore functionality, focusing primarily on changing hosting providers. By April 2024, the C2 servers were relocated again, likely to hinder further detection efforts. As of now, researchers have identified three active hosts—located in Australia, the United States, and Singapore—using the updated certificate.
The report raises questions about the precise relationship between the KV Botnet and Volt Typhoon. While the group is known for its emphasis on stealth and minimal tool usage, the botnet operators have made little effort to obscure their infrastructure following actions by the FBI and researchers. This suggests that the botnet may be managed by a separate entity indirectly linked to Volt Typhoon.