Cybercriminals from Brazil and Asia are disseminating malicious advertisements on Google, disguised as legitimate Google Ads platform promotions. Users who unknowingly enter their credentials on these counterfeit pages inadvertently enable attackers to compromise even more accounts.
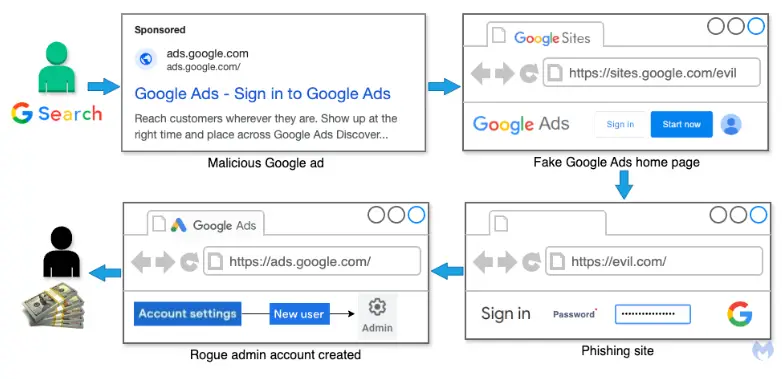
Experts from Malwarebytes Labs uncovered that these fraudulent ads appear in Google search results, mimicking genuine Google Ads promotions. For instance, if a user searches for Google Ads, the top result might be occupied by a fake ad. Clicking on the link redirects the user to a counterfeit login page that closely resembles the official platform.
Here, attackers harvest credentials and create fake administrator accounts. Malwarebytes Labs researchers have dubbed this campaign “the most audacious operation involving malicious advertising,” as it strikes at the core of Google’s business, potentially impacting thousands of the company’s clients.
The stolen accounts are either resold on dark web forums or utilized for subsequent attacks. According to experts, Google Ads accounts are highly valuable assets for cybercriminals.
Although users can verify advertiser information through the three-dot menu, the fake ads often appear legitimate. Frequently, attackers exploit compromised accounts with a significant number of active, legitimate ads. For example, one campaign involved the breach of an account belonging to a Taiwanese electronics company.
Phishing pages are hosted on Google Sites, enabling attackers to generate links with the Google domain, making them almost indistinguishable from authentic ones.
Within just a few days, Malwarebytes Labs identified and reported over 50 fraudulent ads while contacting affected users who had suffered financial losses. Despite these efforts, the attackers remain active. “We quickly realized that no matter how many incidents and blocks were reported, the attackers managed to maintain at least one fraudulent ad active 24/7,” Malwarebytes Labs reported.
Some victims received alerts about suspicious logins from Brazil. Malwarebytes Labs identified two primary groups of attackers: one comprising Portuguese-speaking individuals, presumably based in Brazil, and another operating from Hong Kong. Additionally, a third group from Eastern Europe was found employing sophisticated obfuscation techniques and fake Google Authenticator pages.
Experts emphasize that these schemes often involve multi-layered redirection mechanisms, allowing attackers to obscure their tracks and sustain the operation of fraudulent campaigns.