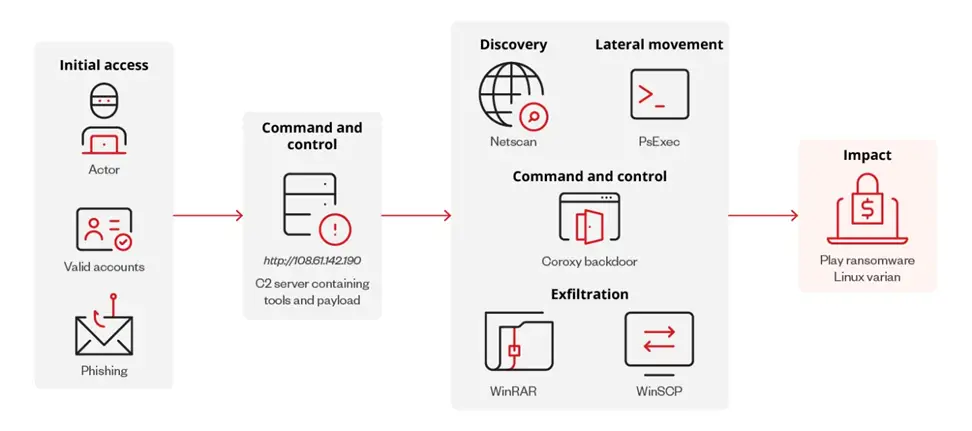
Trend Micro has identified a new variant of the Play (Balloonfly, PlayCrypt) ransomware, now targeting VMware ESXi. The emergence of a Linux version indicates the group’s expanded attack surface, increasing potential victims and enhancing the likelihood of successful ransom negotiations.
First detected in June 2022, Play ransomware is notorious for its double extortion tactics. It encrypts systems after exfiltrating sensitive data, demanding a ransom for the decryption key. By October 2023, approximately 300 organizations had fallen victim to Play.
According to Trend Micro, in the first seven months of 2024, the majority of Play’s victims were in the United States, followed by Canada, Germany, the United Kingdom, and the Netherlands. The affected sectors include manufacturing, professional services, construction, IT, retail, financial services, transportation, media, legal services, and real estate.
The analysis of the new Linux version of Play is based on an RAR file hosted at an IP address (108.61.142[.]190). The archive contains other tools previously used in attacks, such as PsExec, NetScan, WinSCP, WinRAR, and the Coroxy backdoor.
Although no infections have been reported yet, the C2 server hosts the common tools Play employs in its attacks. This suggests that the Linux version may utilize similar tactics, techniques, and procedures (TTPs).
Upon execution, the ransomware operates within the ESXi environment, proceeding to encrypt virtual machine files, including disks, configuration files, and metadata, appending the extension “.PLAY”. A ransom note is then placed in the root directory.
Further analysis suggests that the Play group likely leverages services and infrastructure provided by Prolific Puma, which offers illegal link-shortening services to other cybercriminals to evade detection when distributing malware.
Notably, the use of a Registered Domain Generation Algorithm (RDGA) to create new domain names is becoming more prevalent among various threat actors, including VexTrio Viper and Revolver Rabbit, for phishing, spamming, and malware distribution.
For instance, Revolver Rabbit has registered over 500,000 domains in the “.bond” zone, amounting to approximately 1 million dollars, utilizing these domains as both active and decoy C2 servers for the XLoader (FormBook) stealer. A typical RDGA pattern used by Revolver Rabbit includes one or more dictionary words followed by a five-digit number, with each word or number separated by a hyphen. These domains are easily readable and often focus on specific themes or regions, such as “ai-courses-17621[.]bond”.
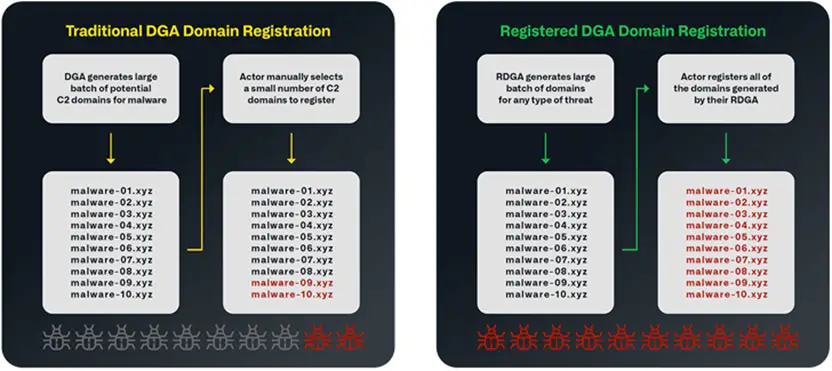
RDGA is harder to detect and defend against compared to traditional DGA, as RDGA enables the generation of numerous domain names for registration and use in infrastructure, either immediately or gradually.
In RDGA, the algorithm is a closely guarded secret known only to the attacker, who registers all the domain names. In traditional DGA, the algorithm is embedded in the malware itself and can be discovered, with most domain names remaining unregistered. While DGA is used exclusively for connecting to malware controllers, RDGA is employed for a wide range of malicious activities.
Recent data indicates potential collaboration between the two cybercriminal groups, suggesting that Play operators are taking steps to circumvent security protocols with the help of Prolific Puma’s services. ESXi environments are highly valuable targets for ransomware attacks due to their critical role in business operations. The ability to encrypt multiple virtual machines simultaneously and the high value of the data they store make them particularly attractive to cybercriminals.


