In Taiwan, a government entity and a religious organization have fallen victim to the Chinese-linked hacker group, Evasive Panda. The attackers employed a previously unknown toolset called CloudScout, designed to compromise cloud services.
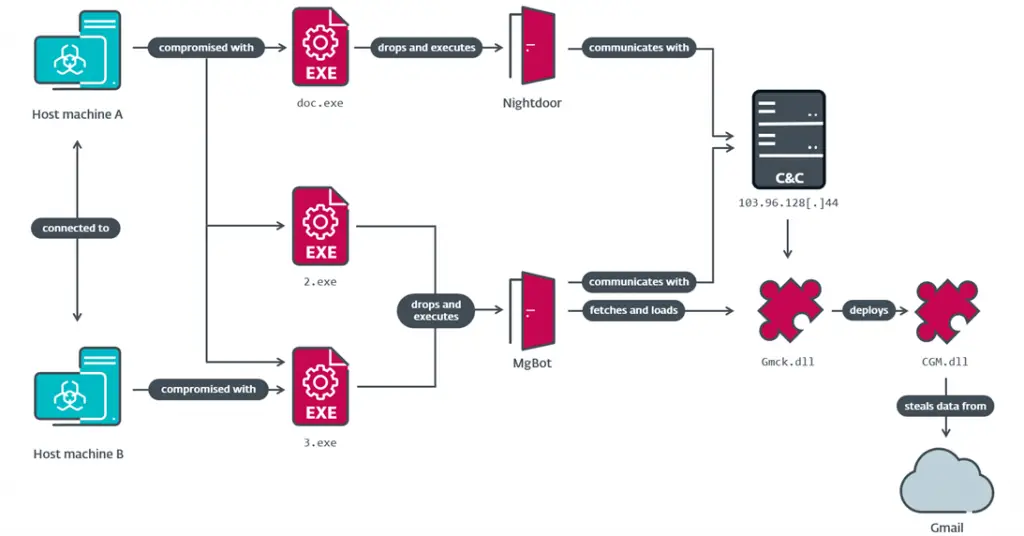
CloudScout leverages stolen session cookies from web browsers to access data stored in the cloud. According to ESET specialists, it integrates seamlessly with the notorious MgBot malware platform, which Evasive Panda utilizes in its attacks.
The analyzed attacks occurred between May 2022 and February 2023. This malicious suite comprises ten C# modules, three of which specifically target data theft from Google Drive, Gmail, and Outlook, while the other modules remain undisclosed.
Evasive Panda, also known by aliases such as Bronze Highland, Daggerfly, and StormBamboo, frequently attacks targets in Taiwan and Hong Kong. The group is notorious for supply chain and DNS-hijacking attacks, often focusing on the Tibetan diaspora and similar groups.
CloudScout modules enable the interception of session cookies, granting unauthorized access to cloud services. Each module connects via a plugin for MgBot, written in C++.
The foundation of CloudScout is the CommonUtilities package, containing unique libraries for HTTP requests and cookie management. These libraries offer greater flexibility than publicly available alternatives.
The data gathered by the attackers—including emails, attachments, and documents (.doc, .xls, .pdf, and others)—is archived into ZIP files for subsequent exfiltration through MgBot or Nightdoor.
ESET researchers note that the introduction of Google’s new security mechanisms, such as Device Bound Session Credentials and App-Bound Encryption, could significantly reduce the effectiveness of such cookie-theft attacks.
In an era of pervasive digitalization, even the most secure systems are vulnerable to targeted cyberattacks. Hacker groups continuously refine their tools, discovering new ways to bypass existing security mechanisms, demanding that organizations remain ever vigilant and implement multilayered data protection systems.


