Overview of the exploit’s control flow
A critical security vulnerability in Kingsoft’s WPS Office, which has already been weaponized by hacker groups. The official statement from WPS claimed that only the international version of WPS 2023 was affected, while other versions remained unaffected.
However, much like in previous instances, Kingsoft has been reluctant to issue comprehensive security advisories to warn users of potential attacks, even though they did release a patch. In this case, Kingsoft failed to disclose that the vulnerability was already being actively exploited.
This prompted the cybersecurity firm ESET, which discovered the vulnerability, to release a detailed report urging users and enterprises to immediately update to the latest version and be wary of attacks originating from a South Korean hacker group. ESET discovered that the vulnerability, CVE-2024-7262, had been exploited by hackers since at least February 2024, categorizing it as a zero-day vulnerability.
ESET dutifully informed Kingsoft of the vulnerability, leading the company to quietly patch it in a new version released in March 2024, though without issuing a public notice about the active exploitation.
Subsequently, ESET found that Kingsoft’s fix was insufficient, leaving the vulnerability still present. The second vulnerability, CVE-2024-7263, was reported to Kingsoft, who completed the patching process in May 2024.
The affected versions ranged from WPS 12.2.0.13110 (released in August 2023) to 12.2.0.17119 (released in May 2024), meaning users should at least upgrade to a version released after May 2024.
Despite the vulnerabilities being patched, there are undoubtedly users and enterprises who, for various reasons, have not yet upgraded to the latest version, leaving the vulnerabilities exploitable. As a result, the South Korean hacker group APT-C-60 has been actively exploiting these flaws.
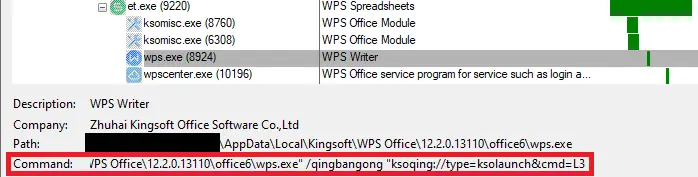
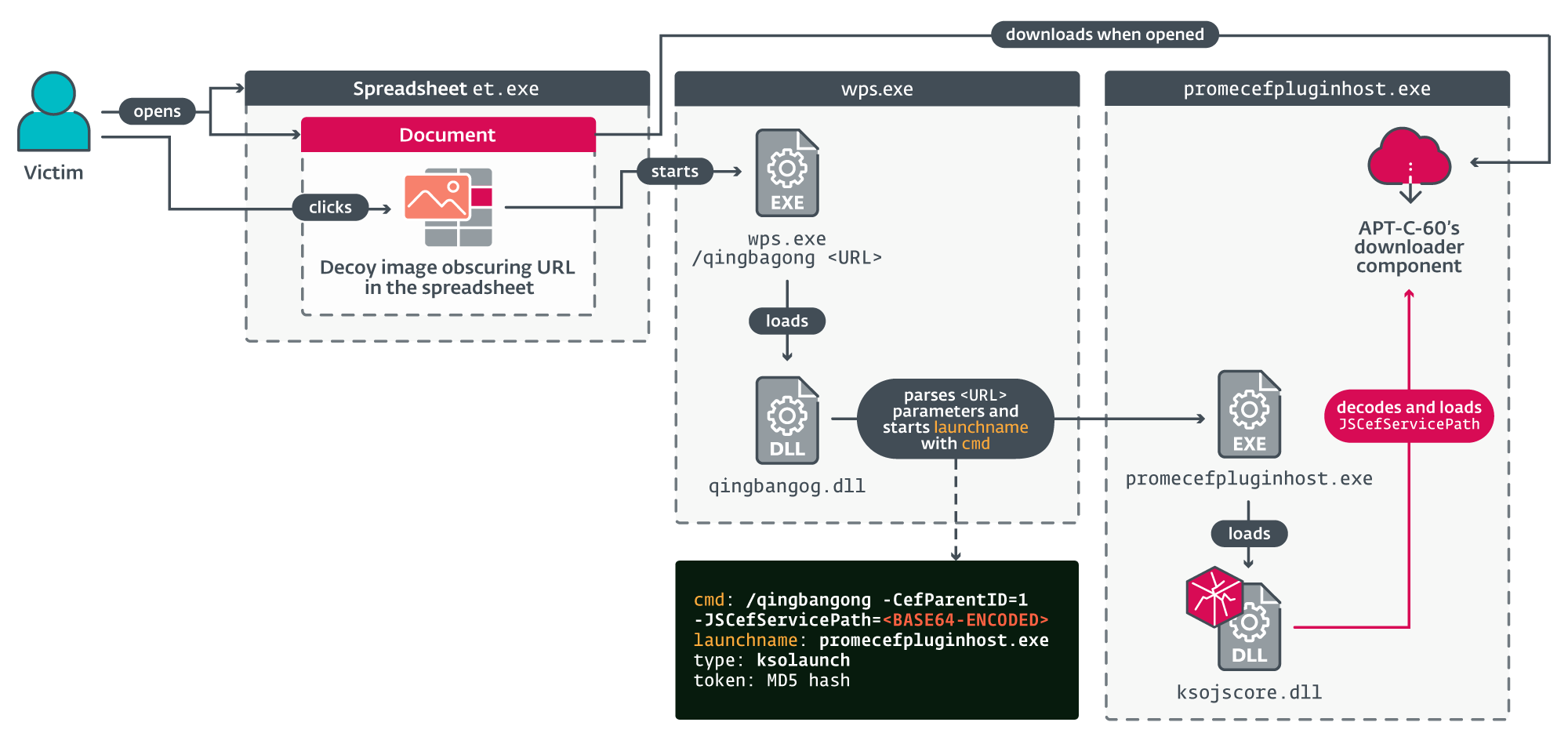
The CVE-2024-7262 vulnerability is associated with WPS’s custom protocol handler, such as ksoqing://, which is designed for quickly launching WPS. Due to inadequate validation and sanitization, hackers can craft malicious hyperlinks that trigger arbitrary code execution (RCE).
In actual attack scenarios, APT-C-60 created MHTML files with embedded bait images and malicious hyperlinks, such as an image that appears to load a document when clicked, but in reality, triggers the malicious hyperlink.
Once clicked, the malicious hyperlink activates the vulnerability, allowing APT-C-60 to execute a specific plugin (promecefpluginhost.exe) via a base64-encoded command, a backdoor program that ESET has named SpyGlace.
ESET also warned that this attack method is highly deceptive, as it can easily lure users into clicking on seemingly harmless files, thereby triggering the vulnerability. For users, particularly enterprise users, it remains crucial to exercise caution when opening emails or files downloaded from the internet.


