Trend Micro specialists have discovered that in a series of attacks, cybercriminals utilized the EDRSilencer tool to disable EDR system alerts. Attackers integrate this tool into their operations to conceal traces of their activities and evade detection.
EDRSilencer is an open-source tool designed similarly to the commercial solution NightHawk FireBlock from MdSec. The program identifies active EDR processes and leverages the Windows Filtering Platform (WFP) to monitor and block network traffic over IPv4 and IPv6 protocols. WFP, used in firewalls and antivirus systems, allows the configuration of persistent filters that control network traffic.
EDRSilencer applies filters to block communication between EDR and the command server. During testing, it successfully prevented data transmission, making the devices appear inactive on the management portal. As a result, the sending of alerts and detailed telemetry is obstructed.
The new version of the tool includes the ability to block 16 modern EDR solutions, including:
- Microsoft Defender;
- SentinelOne;
- FortiEDR;
- Palo Alto Networks Cortex XDR;
- Cisco Secure Endpoint;
- ElasticEDR;
- Carbon Black EDR;
- Trend Micro Apex One.
Experiments also showed that some EDR products continue to transmit reports due to certain executable files missing from the hardcoded list. However, attackers can add filters for the required processes, extending the range of blocked components.
Once additional processes are added to the blocklist, the EDR tools cease sending logs. This suppression allows malicious activity to go unnoticed, significantly increasing the chances of a successful attack without intervention from specialists.
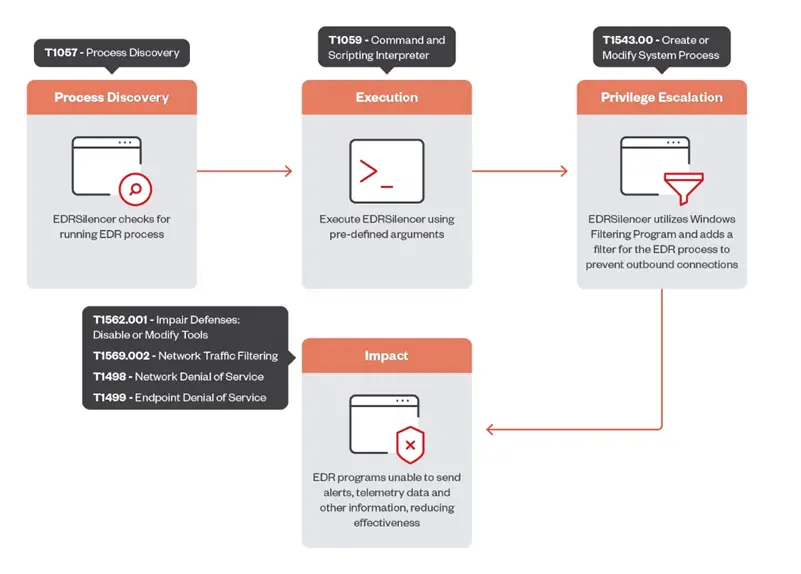
A diagram illustrating the functionality of EDRSilencer in cyberattacks depicts the stages of the process: from detecting active EDR systems to executing code and escalating privileges, resulting in the suppression of telemetry and alerts. Techniques such as T1057 (process discovery), T1059 (command and scripting interpreter), and T1543 (creation or modification of system processes) are included. The diagram shows how EDRSilencer exploits the Windows Filtering Platform to filter network traffic and prevent data transmission to the command server, thereby weakening the defensive capabilities of EDR systems.
Trend Micro recommends classifying EDRSilencer as malware and blocking it at the early stages of an attack. Experts also advise implementing multi-layered security measures to isolate critical systems, employing solutions with behavioral analysis and anomaly detection, and monitoring for indicators of compromise within the network. The principle of least privilege is also a key defense element against such attacks.


