The RansomHub group has begun deploying new malicious software designed to disable EDR solutions on devices, circumvent security mechanisms, and gain full control over the system. The tool, named EDRKillShifter, was uncovered by Sophos experts following a failed attack in May 2024.
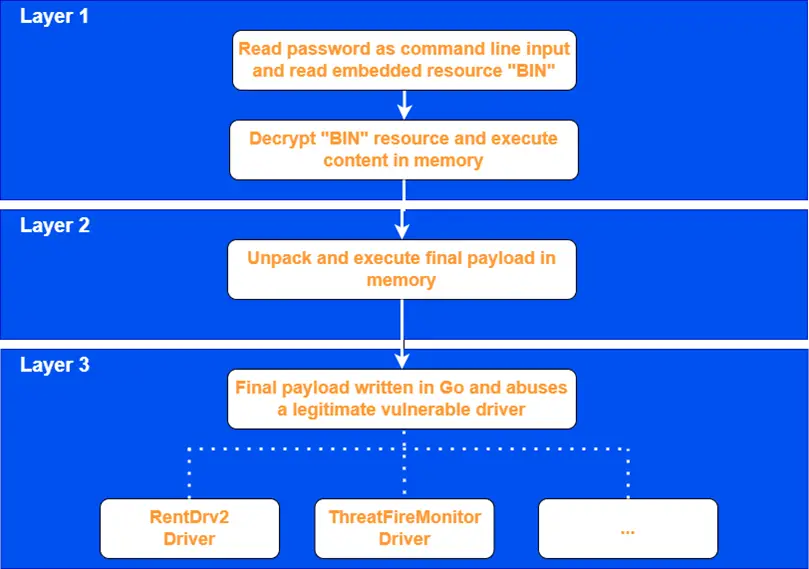
EDRKillShifter is a loader program that facilitates a Bring Your Own Vulnerable Driver (BYOVD) attack, wherein a legitimate but vulnerable driver is exploited to escalate privileges, disable protective measures, and seize full control of the system.
Sophos identified two distinct samples of EDRKillShifter, both of which utilize publicly available PoC exploits from GitHub. One sample exploits the vulnerable RentDrv2 driver, while the other targets the ThreatFireMonitor driver, a component of an obsolete system monitoring package. EDRKillShifter can also load various drivers depending on the attackers’ requirements.
The execution process of EDRKillShifter consists of three stages. First, the attacker runs a binary file with a password to decrypt and execute the embedded BIN resource in memory. Next, the code unpacks and executes the final payload, which loads the vulnerable driver to escalate privileges, disable active processes, and EDR systems.
The malware creates a new service for the driver, starts it, and loads the driver, then enters an infinite loop, continuously monitoring running processes and terminating them if the process names match the encrypted target list.
Sophos advises enabling tamper protection in endpoint security products, maintaining the separation of user and administrator rights to prevent the loading of vulnerable drivers by attackers, and regularly updating systems, as Microsoft frequently revokes certificates of signed drivers that have been used in previous attacks.


