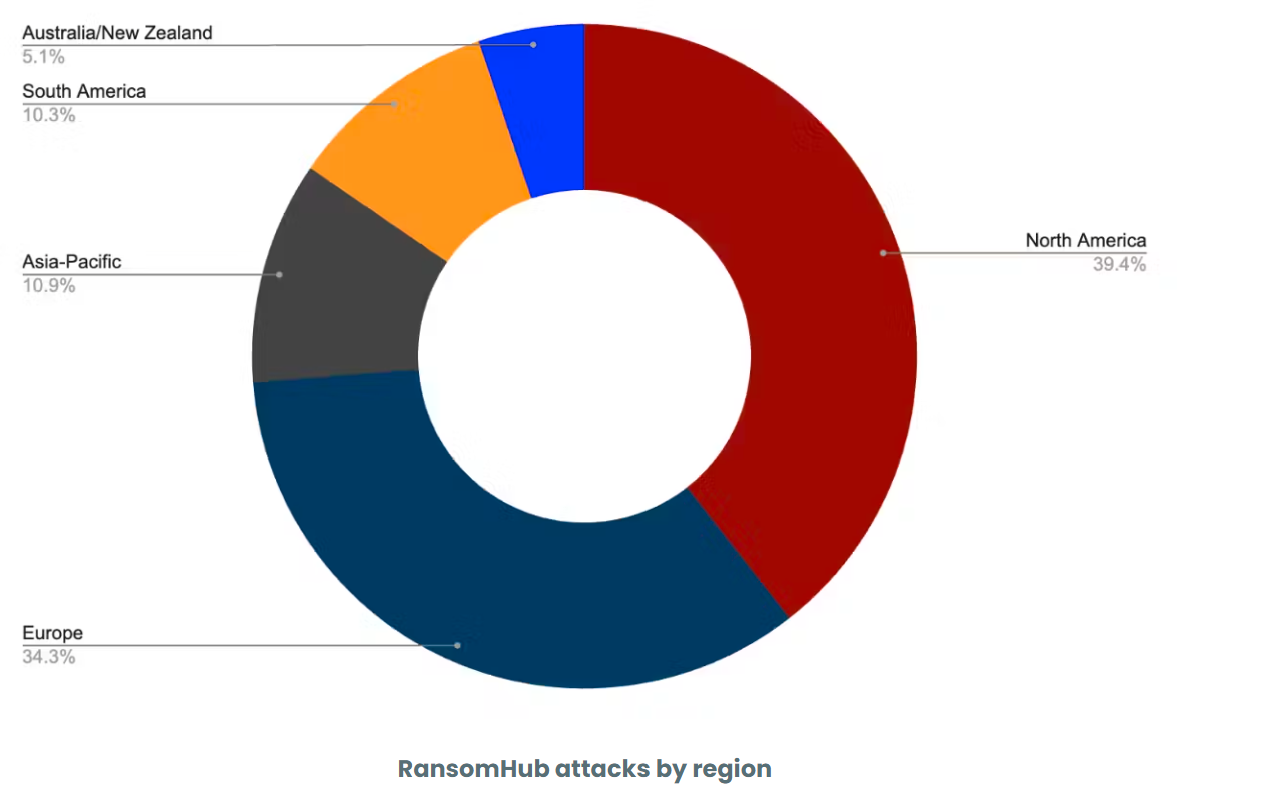
RansomHub attacks by region Source: ZeroFox Intelligence
Since its emergence in February 2024, the ransomware group RansomHub has encrypted and stolen data from over 210 victims, according to U.S. authorities. Among the affected are organizations from diverse sectors, including water supply, information technology, healthcare, government institutions, emergency services, agriculture, and financial entities.
RansomHub operates under the “ransomware-as-a-service” (RaaS) model and was previously known by aliases such as Cyclops and Knight. The group quickly attracted high-profile affiliates, including those with past ties to notorious groups like LockBit and ALPHV (also known as BlackCat).
According to the cybersecurity firm ZeroFox, RansomHub’s activity has surged rapidly. While the group accounted for only 2% of all attacks in the first quarter of 2024, this figure rose to 5.1% in the second quarter and reached 14.2% by the third quarter. Notably, 34% of the group’s attacks target European organizations, a percentage significantly higher than the average across the broader threat landscape.
RansomHub employs a double extortion strategy, wherein data is stolen first, and then the victims’ systems are encrypted. Victims are instructed to contact the malicious operators via a unique onion address to negotiate ransom terms. Should they refuse to pay, their stolen information is published on a dedicated data leak site.
The hackers gain access to victims’ systems by exploiting vulnerabilities in well-known software products such as Apache ActiveMQ, Atlassian Confluence, Citrix ADC, and others. Once inside, they conduct network reconnaissance and scanning with tools like AngryIPScanner and Nmap, while disabling antivirus software to maintain stealthy access.
Additionally, the attackers create user accounts to preserve their foothold in the system and employ various tools to harvest credentials and escalate privileges. Lateral movement within the network is facilitated through techniques such as remote desktop protocol (RDP), PsExec, AnyDesk, and other widely-used management utilities.
A distinctive feature of RansomHub’s attacks is their intermittent encryption, significantly accelerating the process. Meanwhile, data is exfiltrated using tools such as PuTTY, Amazon AWS S3, WinSCP, and others.
Researchers note the hackers’ shift towards more complex, multi-layered extortion schemes amid the evolving landscape of ransomware attacks. These include data encryption and theft, threats of DDoS attacks, and coercion of victims’ business partners to intensify pressure for ransom payment.
The “ransomware-as-a-service” model continues to prove highly lucrative, fueling the emergence of new ransomware variants. It has even drawn the interest of state-backed hacking groups, such as those from Iran, which collaborate with established ransomware operators to claim a share of the illicit proceeds.


