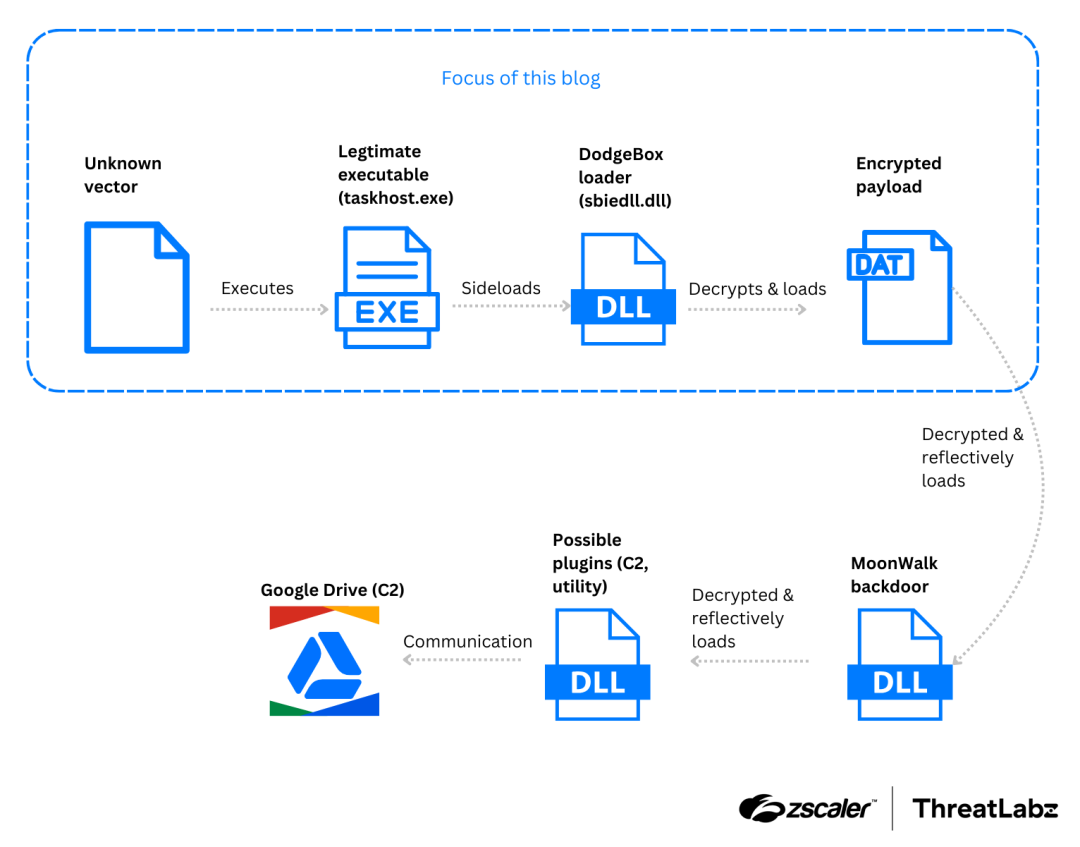
Attack chain used to deploy the DodgeBox loader and MoonWalk backdoor
The China-linked group APT41 is suspected of using an advanced version of the infamous StealthVector malware to deliver a new backdoor named MoonWalk. This new variant of StealthVector has been code-named DodgeBox by Zscaler experts, who discovered it in April 2024.
DodgeBox acts as a loader that deploys the MoonWalk backdoor. Security researchers noted that MoonWalk employs numerous evasion techniques found in DodgeBox and utilizes Google Drive for C2 communications.
Experts state that APT41 has been active since at least 2007. It is also known by other aliases, such as Axiom, Blackfly, and Brass Typhoon. In September 2020, the U.S. Department of Justice announced charges against several members of this group for hacking over 100 companies worldwide. These attacks facilitated the theft of source code, software signing certificates, customer account data, and critical business information.
In recent years, APT41 has been linked to multiple breaches of U.S. state government networks and attacks on Taiwanese media organizations using the GC2 tool. The group’s use of StealthVector was first documented by Trend Micro in August 2021. This loader, written in C/C++, is used to deliver Cobalt Strike Beacon and other malware.
DodgeBox is considered an enhanced version of StealthVector, incorporating techniques such as call stack spoofing, DLL sideloading, and DLL hollowing to evade detection. The methods of propagation for this malware remain unknown.
Researchers report that APT41 uses DLL sideloading to execute DodgeBox, leveraging a legitimate executable (taskhost.exe) signed by Sandboxie to load the malicious library (sbiedll.dll). DodgeBox, a DLL loader written in C, decrypts and initiates the second-stage loader—the MoonWalk backdoor.
The attribution of DodgeBox to APT41 is based on the similarity of the program to StealthVector, the use of DLL sideloading, and the fact that DodgeBox samples were uploaded to VirusTotal from Thailand and Taiwan.
Researchers emphasize that DodgeBox is a novel malicious loader employing multiple evasion techniques and offering various capabilities, including decrypting and loading embedded DLLs, environment checking, and performing cleanup procedures.
As cybercriminals continue to develop tools to bypass existing defense mechanisms, organizations must prioritize monitoring and updating their security systems to counter these ever-evolving threats.


