The research team at Wiz Research has uncovered a critical vulnerability within the infrastructure of the Chinese AI startup DeepSeek. An exposed ClickHouse database granted unrestricted access to highly sensitive information, including chat histories, secret keys, and server data.
DeepSeek has recently garnered significant attention for its development of the advanced AI model DeepSeek-R1, positioned as a competitor to OpenAI’s solutions. However, a security audit of the company has revealed severe flaws.
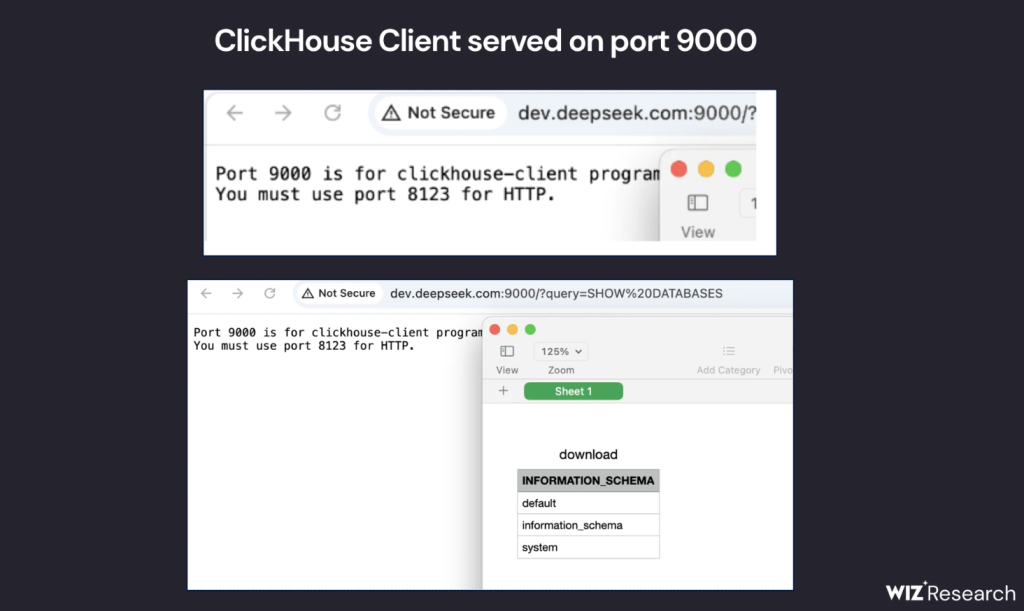
During an external security assessment, researchers identified a publicly accessible database hosted at oauth2callback.deepseek.com:9000 and dev.deepseek.com:9000. The database was accessible without any authentication mechanisms, leaving it vulnerable to unauthorized control and manipulation.
The exposed database contained over a million records, encompassing user interactions with the AI, API keys, server metadata, and other sensitive details. Particularly alarming was the availability of logs detailing API endpoint names and their operational parameters.
Furthermore, the vulnerability allowed threat actors to execute SQL queries without restriction, potentially leading to a large-scale data breach, password exfiltration, and exposure of the servers’ internal file structures.
Wiz Research’s investigation commenced with an analysis of DeepSeek’s publicly available domains. A total of 30 externally accessible subdomains were identified, including the chatbot interface, service status page, and API documentation. Initially, these did not present a security risk.
However, further scrutiny revealed open ports 8123 and 9000 on multiple DeepSeek servers. Subsequent analysis linked these ports to ClickHouse, a powerful analytics-oriented database management system developed by Yandex and widely used for handling large-scale data operations.
Leveraging ClickHouse’s HTTP interface, researchers were able to execute SQL queries directly through a web browser. A simple SHOW TABLES; command exposed a full list of available tables, drawing particular attention to log_stream.
This table contained highly sensitive data, including log timestamps, API endpoint names, plaintext chat contents, operational metadata, and details about DeepSeek’s internal services.
The most critical risk posed by this vulnerability was privilege escalation, which could have granted attackers complete control over DeepSeek’s servers, bypassing all security protections.
Upon discovering the issue, the Wiz Research team promptly alerted DeepSeek, which responded swiftly by revoking public access to the database and patching the vulnerability.
Update: Yandex has clarified that ClickHouse is not a database itself but an open-source database management system. As an independent open-source product, ClickHouse requires businesses to configure their own security settings and bear full responsibility for data protection.