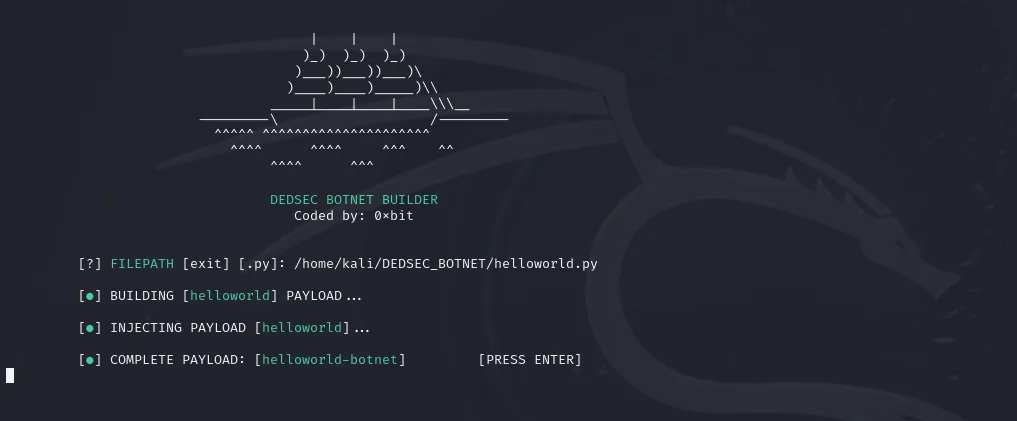
Linux-targeted malware has surged in recent years, with prevalent threats including cryptominers, backdoors, rootkits, and botnets. Recently, a new tool, DEDSEC_BOTNET, has emerged, designed for constructing sophisticated and elusive Linux-based botnets.
Recent attacks on DeepSeek have demonstrated the active use of botnets for DDoS attacks, including SSDP and NTP reflection, and HTTP proxy attacks. DEDSEC_BOTNET’s emergence raises significant cybersecurity concerns. This builder facilitates embedding malicious code within legitimate Python scripts and other software, ensuring maximum stealth and persistence within compromised systems.
Malicious payloads crafted with this tool possess several key characteristics: system concealment, reboot persistence via autostart mechanisms, and DDoS attack participation, overwhelming target servers with a flood of requests. This approach allows for powerful, elusive, distributed network creation.
Such botnets are not novel in the Linux landscape. Notable malware families include XorDDoS, Mirai, Mozi, Kaiji, Fodcha, and RedGoBot. However, DEDSEC_BOTNET’s deep integration capabilities within legitimate programs set it apart. Using this builder, malicious actors can create malware capable of covert, long-term presence within compromised system infrastructures.
The tool’s execution involves several steps: downloading the builder, its activation, and the provision of command sets for managing the malicious payload. The process generates a file injected into the target system and activated upon legitimate software launch.
Experts recommend Linux system administrators enhance installed software oversight, regularly audit server processes, and implement safeguards against unauthorized file modification. Tracking emerging threats is crucial, as cybercriminals continually refine methods and devise ways to circumvent traditional defenses.