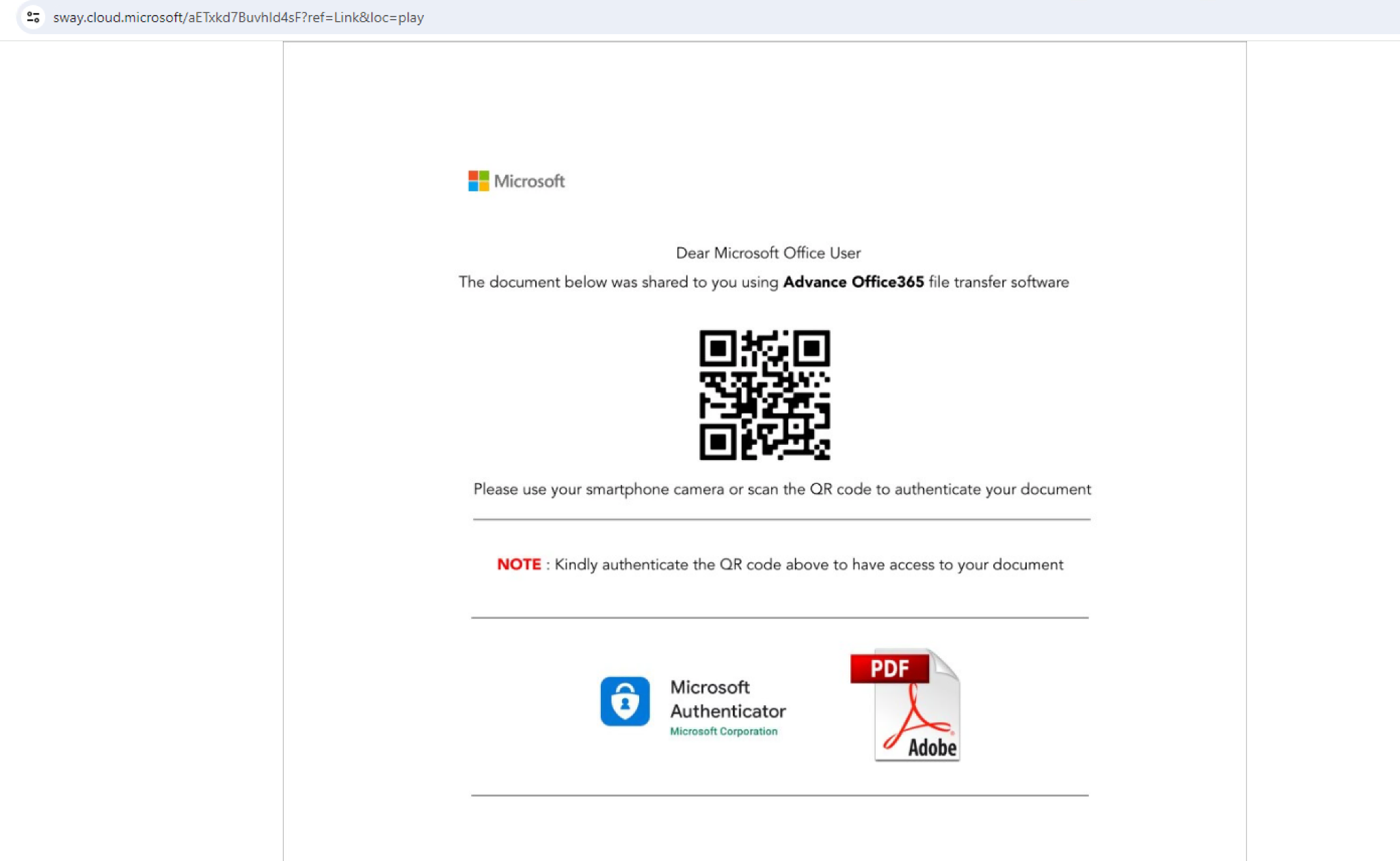
Sway page with QR code containing phishing URL | Image: Netskope
In July 2024, Netskope experts identified a sharp surge in phishing attacks exploiting Microsoft Sway to steal Microsoft 365 user credentials. The recorded 2000-fold increase in attacks starkly contrasted with the minimal activity seen in the first half of the year, underscoring the scale and severity of this campaign.
These attacks predominantly targeted users in Asia and North America, with cybercriminals focusing particularly on the technology, manufacturing, and financial sectors. Phishing emails redirected potential victims to pages hosted on the “sway.cloud.microsoft” domain, where users were prompted to scan QR codes leading to malicious websites.
The attackers actively exploited vulnerabilities in mobile devices, which are associated with weaker security measures compared to computers. This heightened the likelihood of bypassing protective mechanisms and facilitated easier access to phishing sites. QR codes embedded in images also helped evade automated email scanners that typically check only text content.
Security researchers explained that users become more vulnerable when scanning QR codes with mobile devices, especially their personal smartphones, due to the inadequate protection on these devices.
Furthermore, the attackers employed various tactics to enhance the effectiveness of their campaign. For instance, they used the method of transparent phishing, which not only allowed them to steal credentials and multi-factor authentication codes but also simultaneously display the legitimate Microsoft login page to the victim, reducing suspicion.
To mask their phishing pages, the attackers also utilized the Cloudflare Turnstile tool, which protects websites from bots. This enabled them to conceal malicious content from static scanners and maintain the domain’s reputation at a high level, avoiding blocks from filtering services like Google Safe Browsing.
It is worth noting that Microsoft Sway had already been used in similar attacks five years ago, during the PerSwaysion campaign, when cybercriminals attempted to steal Office 365 credentials through a phishing kit offered as a service. At that time, at least 156 high-profile individuals from financial, legal, and real estate companies in several countries, including the United States, Canada, Germany, and the United Kingdom, were affected.
This latest wave of attacks once again highlights the critical need for heightened security awareness and caution when interacting with suspicious emails and links, especially those that require QR code scanning.


