The Turla hacking group has adopted a sophisticated new strategy, leveraging the infrastructure of other cybercriminals to conduct covert operations. Research by Lumen reveals that the group infiltrated the networks of the Pakistani outfit Storm-0156, repurposing their resources for its own campaigns.
Since December 2022, Turla has utilized Storm-0156’s command-and-control servers to target previously compromised entities, including government agencies in Afghanistan and India. The group deployed its signature malicious tools—TinyTurla, TwoDash, and Statuezy—which facilitated stealthy network infiltration, device control, and data exfiltration.
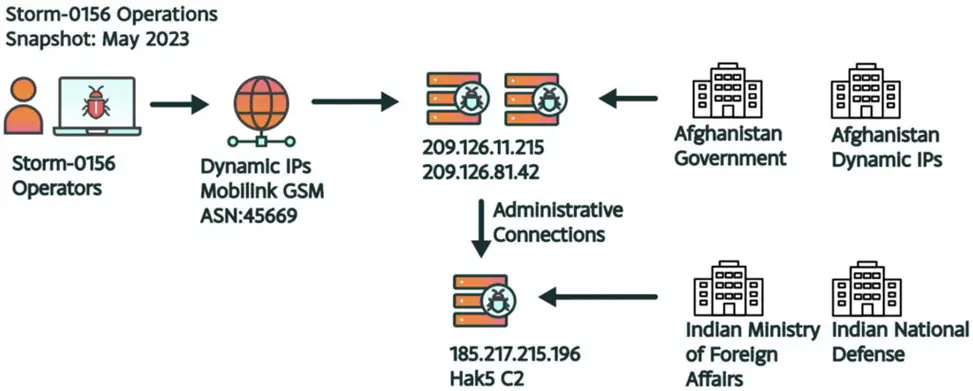
A diagram from Storm-0156’s operations in May 2023 illustrates the connection between Storm-0156 operators and dynamic IPs from Mobilink GSM (ASN: 45669). These link to command servers at 209.126.11.215 and 209.126.81.42, which, in turn, connect to Afghan governmental institutions and India’s Ministries of Foreign Affairs and Defense through the node 185.217.215.196 associated with Hak5 Cloud C2.
Experts from Microsoft and Lumen highlight that Turla not only commandeered Storm-0156’s servers but also penetrated their workstations, gaining access to critical assets, including stolen credentials, CrimsonRAT and Wainscot malware, and files containing sensitive information.
Analysts explain that national hacking groups often neglect advanced security measures to conceal their methodologies, leaving them exposed to rival attacks. This tactic enables Turla to obscure its own tools while shifting the blame for its operations onto others.
Turla’s use of third-party infrastructure extends beyond Storm-0156. In 2019, the group targeted international entities using resources from the Iranian group OilRig. Similarly, in 2022, it exploited vulnerabilities in victims of the Andromeda malware for its operations.


